AP-7131N-FGR Access Point Product Reference Guide
6-20
4.
Click
Apply
to save any changes to the Subnet Access screen. Navigating away from the
screen without clicking the Apply button results in all changes to the screens being lost.
5.
Click
Undo Changes
(if necessary) to undo any changes made. Undo Changes reverts the
settings displayed on the Subnet Access screen to the last saved configuration.
6.
Click
Logout
to securely exit the Access Point applet. A prompt displays confirming the
logout before the applet is closed.
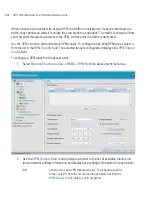
6.6.1.1 Available Protocols
Protocols that are not pre-configured can be specified using the drop down list within the
Transport
column within the Subnet Access and Advanced Subnet Access screens. They include:
•
ALL
- Enables all of the protocol options displayed in the drop-down menu (as described
below).
•
TCP
-
Transmission Control Protocol
is
a set of rules for sending data as message units over
the Internet. TCP manages individual data packets. Messages are divided into packets for
efficient routing through the Internet.
•
UDP
-
User Datagram Protocol
is used for broadcasting data over the Internet. Like TCP, UDP
runs on top of
Internet Protocol
(IP) networks. Unlike TCP/IP, UDP/IP provides few error
recovery services. UDP offers a way to directly connect, and then send and receive
datagrams over an IP network.
•
ICMP
-
Internet Control Message Protocol
is tightly integrated with IP. ICMP messages are
used for out-of-band messages related to network operation. ICMP packet delivery is
unreliable. Hosts cannot count on receiving ICMP packets for a network problem.
•
AH
- Authentication Header is one of the two key components of
IP Security Protocol
(IPsec).
The other key component is
Encapsulating Security Protocol (ESP)
.
AH provides authentication, proving the packet sender really is the sender, and the data
really is the data sent. AH can be used in transport mode, providing security between two
end points. Also, AH can be used in tunnel mode, providing security like that of a
Virtual
Private Network
(VPN).
•
ESP
-
Encapsulating Security Protocol
is one of two key components of
IP Security Protocol
(IPsec). The other key component is
Authentication Header
(AH). ESP encrypts the packets
and provides authentication services. ESP can be used in transport mode, providing security
End Port
Enter the ending port number for a port range. If the protocol uses
a single port, leave the field blank. A new entry might use
Web
Traffic
for its name,
TCP
for its protocol, and
80
for its port number.
Summary of Contents for AP-7131N-FGR
Page 1: ...AP 7131N FGR Access Point Product Reference Guide ...
Page 3: ...AP 7131N FGR Access Point Product Reference Guide 72E 126727 01 Revision A September 2009 ...
Page 4: ......
Page 55: ...Hardware Installation 2 11 ...
Page 68: ...AP 7131N FGR Access Point Product Reference Guide 2 24 ...
Page 90: ...AP 7131N FGR Access Point Product Reference Guide 3 22 ...
Page 148: ...AP 7131N FGR Access Point Product Reference Guide 4 58 ...
Page 300: ...AP 7131N FGR Access Point Product Reference Guide 6 72 ...
Page 338: ...AP 7131N FGR Access Point Product Reference Guide 7 38 ...
Page 635: ...Configuring Mesh Networking 9 23 5 Define a channel of operation for the 802 11a n radio ...
Page 648: ...AP 7131N FGR Access Point Product Reference Guide 9 36 ...
Page 672: ...AP 7131N FGR Access Point Product Reference Guide 10 24 line con 0 line vty 0 24 end ...
Page 692: ...AP 7131N FGR Access Point Product Reference Guide B 14 ...
Page 698: ...AP 7131N FGR Access Point Product Reference Guide B 20 ...
Page 702: ...AP 7131N FGR Access Point Product Reference Guide C 4 ...
Page 707: ......