Configuration Guide
532
Configuring ACL
Configuration Example for ACL
2) Configure permit rules to match packets with source IP address 10.10.70.0/24, and
destination ports TCP 80, TCP 443 and TCP/UDP 53. These rules allow the Marketing
department to visit http and HTTPS websites on the Internet.
3) Configure a deny rule to match packets with source IP address 10.10.70.0. This rule
blocks other network services.
The switch matches the packets with the rules in order, starting with Rule 1. If a packet
matches a rule, the switch stops the matching process.
Binding Configuration
Apply the Extend-IP ACL to a Policy and bind the Policy to port 1/0/1 so that the ACL rules
will apply to the Marketing department only.
Demonstrated with T1600G-52TS, this chapter explains configuration procedures in two
ways: using the GUI and using the CLI.
3.4 Using the GUI
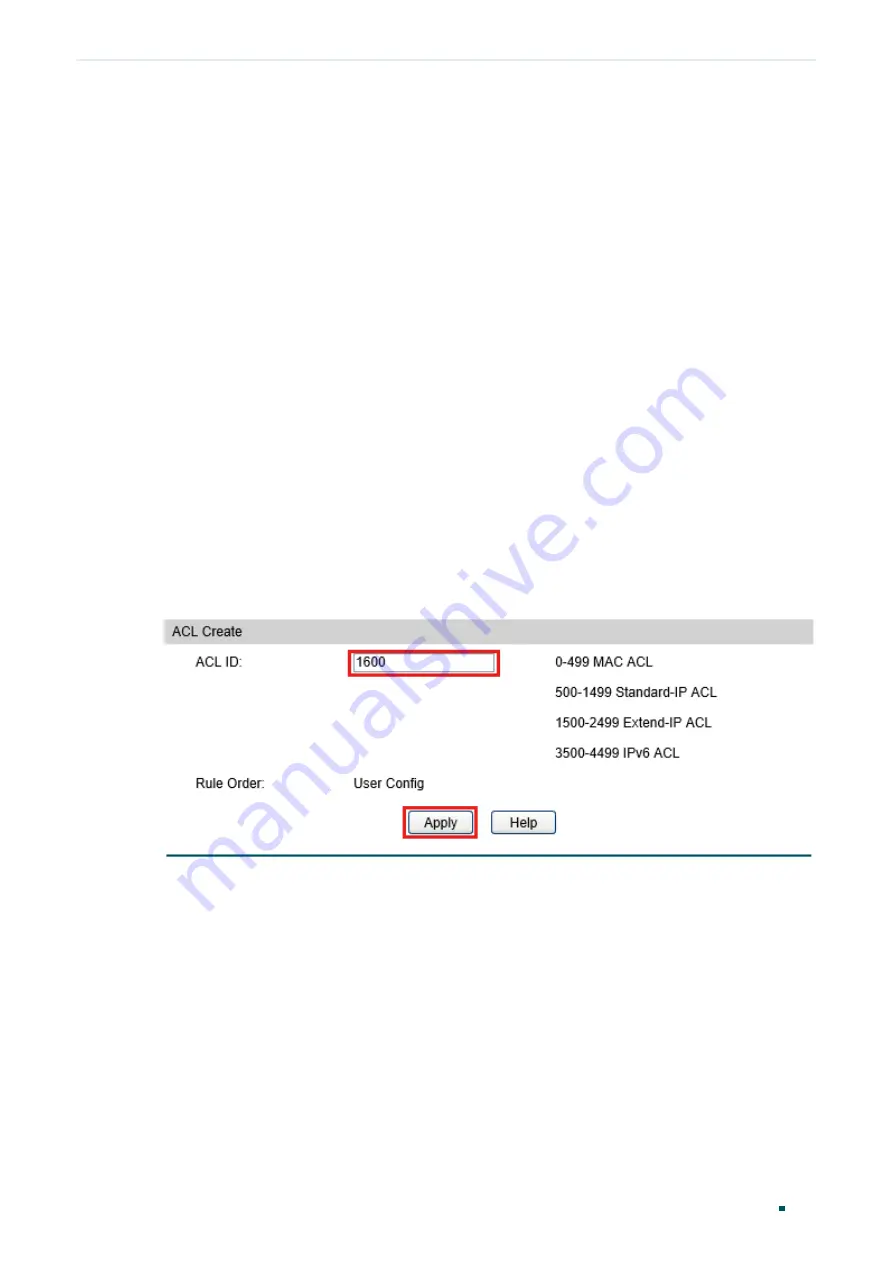
1) Choose the menu
ACL > ACL Config > ACL Create
to load the following page. Then
create Extend- IP ACL 1600.
Figure 3-2
Creating an Extend-IP ACL
2) Choose the menu
ACL > ACL Config > Extend-IP ACL
to load the the following page.
Configure Rule 1 to match packets with the source IP address 10.10.70.0/24 and
destination IP address 10.10.80.0/24.






























