RADIUS
User
FortiGate Version 4.0 Administration Guide
572
01-400-89802-20090424
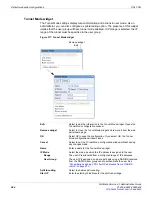
Figure 376: Example RADIUS server list
Configuring a RADIUS server
The RADIUS server uses a “shared secret” key to encrypt information passed between it
and clients such as the FortiGate unit. When you configure a RADIUS server, you can also
configure a secondary RADIUS server. The FortiGate unit attempts authentication with the
primary server first, and if there is no response, uses the secondary server. You can
include the RADIUS server in every user group without including it specifically in user
group configurations.
The RADIUS server can use several different authentication protocols during the
authentication process:
•
MS-CHAP-V2 is the Microsoft challenge-handshake authentication protocol v2
•
MS-CHAP is the Microsoft challenge-handshake authentication protocol v1
•
CHAP (challenge-handshake authentication protocol) provides the same functionality
as PAP, but does not send the password and other user information over the network to
a security server
•
PAP (password authentication protocol) is used to authenticate PPP connections. PAP
transmits passwords and other user information in clear text (unencrypted).
If you have not selected a protocol, the default protocol configuration uses PAP, MS-
CHAPv2, and CHAP, in that order.
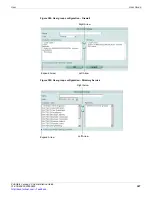
To add a new RADIUS server, go to
User > Remote > RADIUS
,
select
Create New
, and
enter or select the following:
Create New
Add a new RADIUS server. The maximum number is 10.
Name
Name that identifies the RADIUS server on the FortiGate unit.
Server Name/IP
Domain name or IP address of the RADIUS server.
Delete icon
Delete a RADIUS server configuration.
You cannot delete a RADIUS server that has been added to a user group.
Edit icon
Edit a RADIUS server configuration.
Edit
Delete
Note: The server secret key should be a maximum of 16 characters in length.
Summary of Contents for Gate 60D
Page 705: ...www fortinet com...
Page 706: ...www fortinet com...