Auto Key
IPSec VPN
FortiGate Version 4.0 Administration Guide
540
01-400-89802-20090424
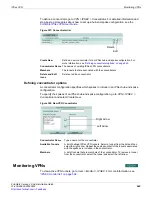
P2 Proposal
Select the encryption and authentication algorithms that will be proposed to
the remote VPN peer. You can specify up to three proposals. To establish a
VPN connection, at least one of the proposals that you specify must match
configuration on the remote peer.
Initially there are two proposals.
Add
and
Delete
icons are next to the
second
Authentication
field. To specify only one proposal, select
Delete
to
remove the second proposal. To specify a third proposal, select
Add
.
It is invalid to set both
Encryption
and
Authentication
to NULL.
Encryption
Select one of the following symmetric-key algorithms:
NULL
— Do not use an encryption algorithm.
DES
— Digital Encryption Standard, a 64-bit block algorithm that uses a 56-
bit key.
3DES
— Triple-DES, in which plain text is encrypted three times by three
keys.
AES128
— a 128-bit block Cipher Block Chaining (CBC) algorithm that uses
a 128-bit key.
AES192
— a 128-bit block Cipher Block Chaining (CBC) algorithm that uses
a 192-bit key.
AES256
— a 128-bit block Cipher Block Chaining (CBC) algorithm that uses
a 256-bit key.
Authentication
Select one of the following message digests to check the authenticity of
messages during an encrypted session:
NULL
— Do not use a message digest.
MD5
— Message Digest 5, the hash algorithm developed by RSA Data
Security.
SHA1
— Secure Hash Algorithm 1, which produces a 160-bit message
digest.
Enable replay
detection
Optionally enable or disable replay detection. Replay attacks occur when an
unauthorized party intercepts a series of IPSec packets and replays them
back into the tunnel.
Enable perfect
forward secrecy
(PFS)
Enable or disable PFS. Perfect forward secrecy (PFS) improves security by
forcing a new Diffie-Hellman exchange whenever keylife expires.
DH Group
Select one Diffie-Hellman group (1, 2, or 5). This must match the DH Group
that the remote peer or dialup client uses.
Keylife
Select the method for determining when the phase 2 key expires:
Seconds
,
KBytes
, or
Both
. If you select
Both
, the key expires when either the time has
passed or the number of KB have been processed. The range is from 120 to
172 800 seconds, or from 5120 to 2 147 483 648 KB.
Autokey Keep Alive
Select the check box if you want the tunnel to remain active when no data is
being processed.
DHCP-IPSec
Provide IP addresses dynamically to VPN clients. This is available for
phase 2 configurations associated with a dialup phase 1 configuration.
You also need configure a DHCP server or relay on the private network
interface. You must configure the DHCP parameters separately. For more
information, see
.
If you configure the DHCP server to assign IP addresses based on RADIUS
user group attributes, you must also set the Phase 1
Peer Options
to
Accept
peer ID in dialup group
and select the appropriate user group. See
a new phase 1 configuration” on page 534
If the FortiGate unit acts as a dialup server and you manually assigned
FortiClient dialup clients VIP addresses that match the network behind the
dialup server, selecting the check box will cause the FortiGate unit to act as
a proxy for the dialup clients.
Note:
You can configure settings so that VPN users can browse the Internet through the
FortiGate unit. For more information, see
Summary of Contents for Gate 60D
Page 705: ...www fortinet com...
Page 706: ...www fortinet com...