4.
Select the settings that you want to import, and then click
Next
.
5.
Click
OK
.
The settings are applied to the printer.
Related Information
&
“Application for Configuring Printer Operations (Web Config)” on page 221
Advanced Security Settings
This section explains advanced security features.
Security Settings and Prevention of Danger
When a printer is connected to a network, you can access it from a remote location. In addition, many people can
share the printer, which is helpful in improving operational efficiency and convenience. However, risks such as
illegal access, illegal use, and tampering with data are increased. If you use the printer in an environment where
you can access the Internet, the risks are even higher.
For printers that do not have access protection from the outside, it will be possible to read the print job logs that
are stored in the printer from the Internet.
In order to avoid this risk, Epson printers have a variety of security technologies.
Set the printer as necessary according to the environmental conditions that have been built with the customer's
environment information.
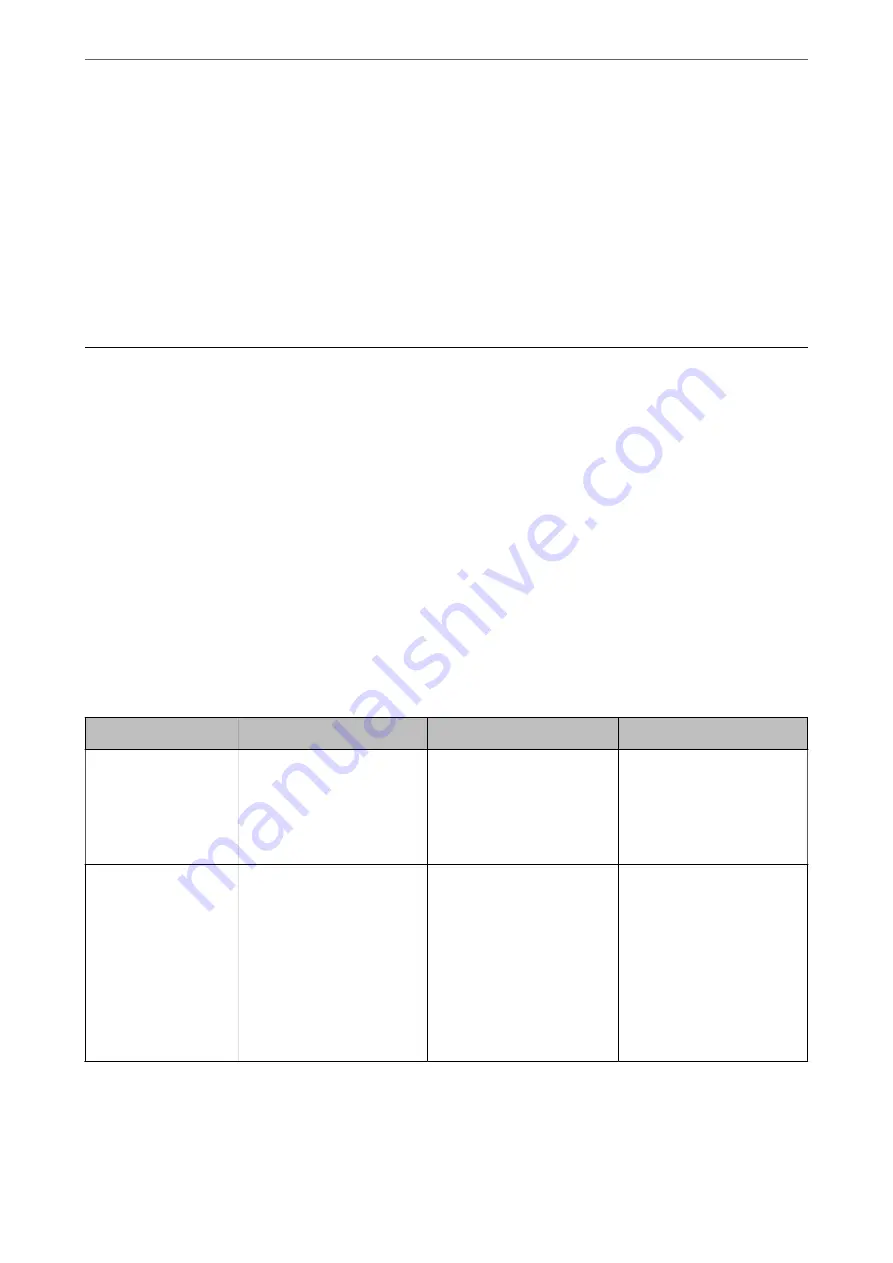
Name
Feature type
What to set
What to prevent
Control of protocol
Controls the protocols and
services to be used for
communication between
printers and computers, and
it enables and disables
features.
A protocol or service that is
applied to features allowed or
prohibited separately.
Reducing security risks that
may occur through
unintended use by
preventing users from using
unnecessary functions.
SSL/TLS
communications
The communication content
is encrypted with SSL/TLS
communications when
accessing to the Epson server
on the Internet from the
printer, such as
communicating to the
computer via web browser,
using Epson Connect, and
updating firmware.
Obtain a CA-signed
certificate, and then import it
to the printer.
Clearing an identification of
the printer by the CA-signed
certification prevents
impersonation and
unauthorized access. In
addition, communication
contents of SSL/TLS are
protected, and it prevents the
leakage of contents for
printing data and setup
information.
>
>
Security Settings and Prevention of Danger
255