DGS-3312SR Stackable Gigabit Layer 3 Switch
62
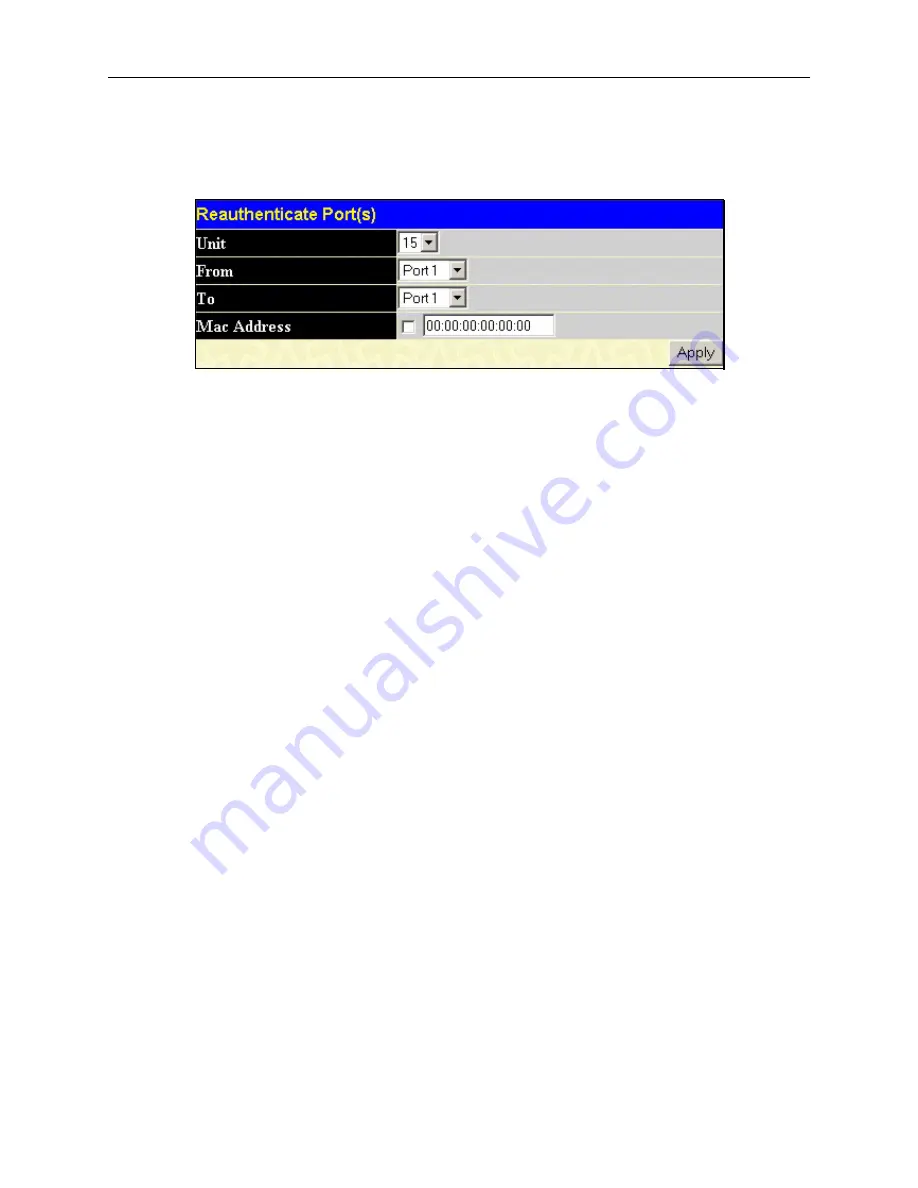
Reauthenticate Port(s) for MAC-based 802.1x
To reauthenticate ports for the MAC side of 802.1x, the user must first enable 802.1x by MAC address in the
Advanced
Settings
window. Click
Configuration >
Port Access Entity > PAE System Control > Reauthenticate Port(s)
to open
the following window:
Figure 4- 26. Reauthenticate Ports – MAC based 802.1x
To reauthenticate ports, first choose the Switch in the Switch stack by using the
Unit
pull-down menu, then the range of
ports in the
From
and
To
field. Then the user must specify the MAC address to be reauthenticated by entering it into the
MAC Address
field and checking the corresponding check box. To begin the reauthentication, click
Apply
.






























