Access Controller
·
User Manual
114
Appendix B
Custom Wiegand Rule
Descriptions
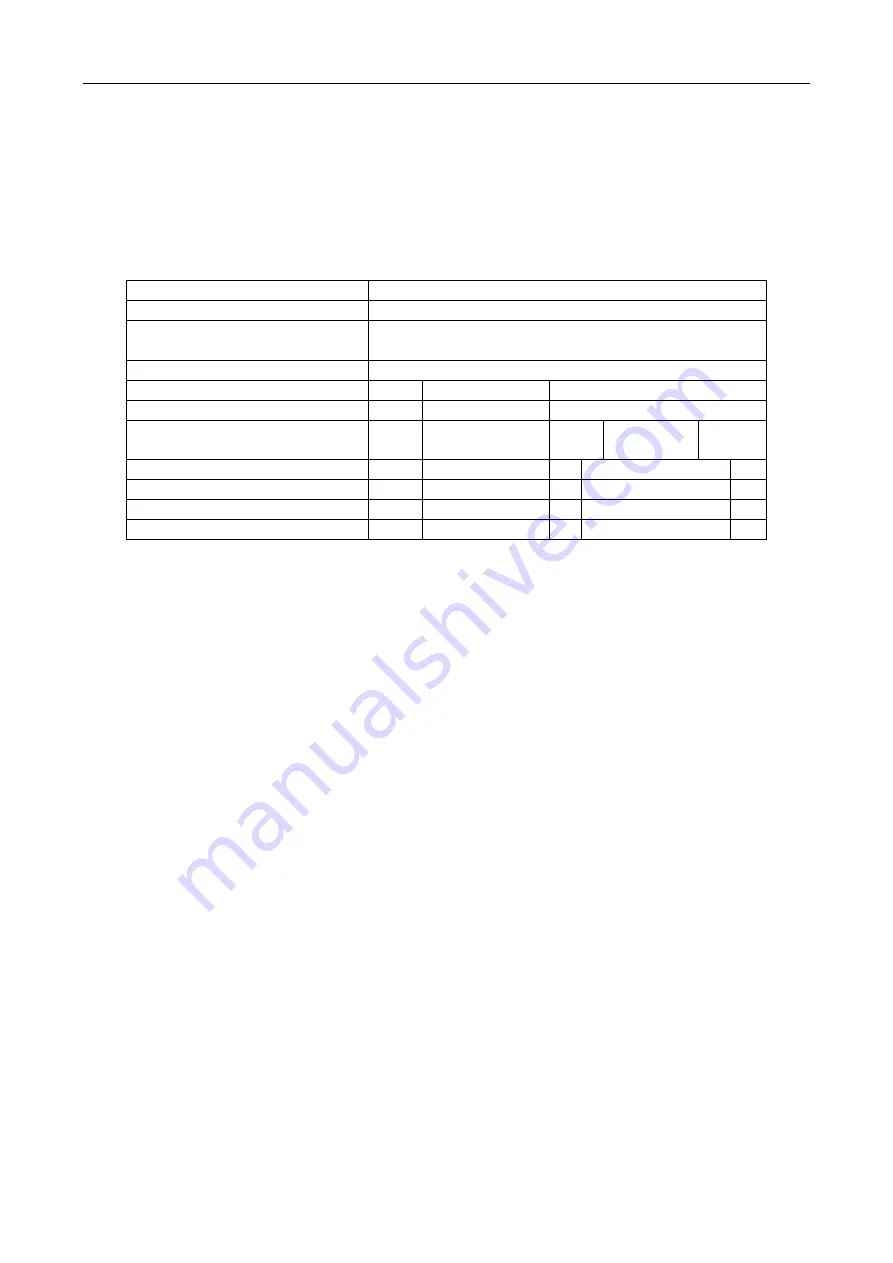
Take Wiegand 44 as an example, the setting values in the Custom Wiegand tab are as follows:
Custom Wiegand Name:
Wiegand 44
Total Length
44
Transformation
Rule
(Decimal
Digit)
byFormatRule[4]=[1][4][0][0]
Parity Mode
XOR Parity
Odd Parity Start Bit
Length
Even Parity Start Bit
Length
XOR Parity Start Bit
0
Length
per
Group
4
Total Length 40
Card ID Start Bit
0
Length
32 Decimal Digit
10
Site Code Start Bit
Length
Decimal Digit
OEM Start Bit
Length
Decimal Digit
Manufacturer Code Start Bit
32
Length
8
Decimal Digit
3
Wiegand Data = Valid Data + Parity Data
Total Length:
Wiegand data length.
Transportation Rule:
4 bytes. Display the combination types of valid data. The example displays the combination
of Card ID and Manufacturer Code. The valid data can be single rule, or combination of multiple rules.
Parity Mode:
Valid parity for wiegand data. You can select either odd parity or even parity.
Odd Parity Start Bit, and Length:
If you select Odd Parity, these items are available. If the odd parity start bit is 1,
and the length is 12, then the system will start odd parity calculation from bit 1. It will calculate 12 bits. The
result will be in bit 0. (Bit 0 is the first bit.)
Even Parity Start Bit, and Length:
If you select Even Parity, these items are available. If the even parity start bit is
12, and the length is 12, then the system will start even parity calculation from bit 12. It will calculate 12 bits. The
result will be in the last bit.
XOR Parity Start Bit, Length per Group, and Total Length:
If you select XOR Parity, these items are available.
Depending on the table displayed above, the start bit is 0, the length per group is 4, and the total length is 40. It
means that the system will calculate from bit 0, calculate every 4 bit, and calculate 40 bits in total (10 groups in
total). The result will be in the last 4 bits. (The result length is the same as the length per group.)
Card ID Start Bit, Length, and Decimal Digit:
If you use the transformation rule, these items are available.
Depending on the table displayed above, the card ID start bit is 0, the length is 32, and the decimal digit is 10. It
represents that from bit 0, there are 32 bits represent the card ID. (The length here is calculated by bit.) And the
decimal digit length is 10 bits.
Site Code Start Bit, Length, and Decimal Digit:
If you use the transformation rule, these items are available. For
detailed information, see the explanation of the card ID.
OEM Start Bit, Length, and Decimal Digit:
If you use the transformation rule, these items are available. For
detailed information, see the explanation of the card ID.
Manufacturer Code Start Bit, Length, and Decimal Digit:
If you use the transformation rule, these items are

















