Configure
Except on the first page, right running head:
Heading1 or Heading1NewPage text (automatic)
17
Alcatel-Lucent
Beta
Beta
OmniAccess 5740 Unified Services Gateway Web GUI Users Guide
C
HASSIS
C
ONFIGURATION
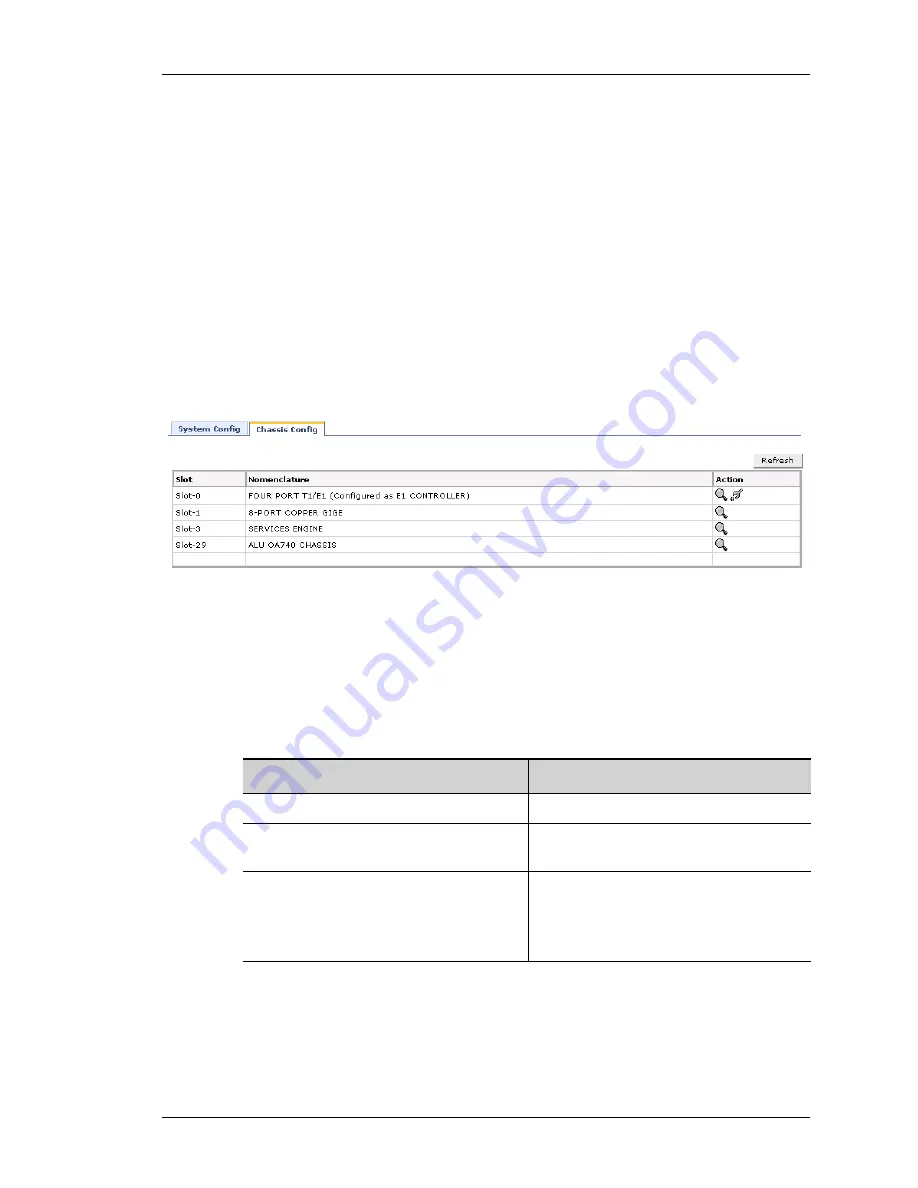
This page lists the respective slot numbers and the line cards associated with it
that are installed in the system.
This also displays the details of the OmniAccess 5740 USG base system that
includes the following components: OmniAccess 5740 USG Chassis, Switch
Fabric, Services Engine, Fan Tray and Power Tray.
V
IEWING
C
HASSIS
C
ONFIGURATION
Step 1:
From the USGM menu bar, click
Configure
. All submenu/links under
Configure are displayed in the left navigation panel.
Step 2:
By default,
System
sub-menu is selected.
System page has two tabs:
System Config
and
Chassis Config
. Click
Chassis
Config
tab. The following page is displayed in the center panel.
Figure 6: Chassis Config
The table below provides description of all the fields in the Chassis Config page.
Table 3: System Config Field Description
Field
Description
Slot
The slot number of the line card.
Nomenclature
The name of the line card/system
component.
Action
Provides an option to view the details of
the respective card.
Note:
Provides an option to set the card
type to T1 or E1.






























