Prestige 652H/HW Series User’s Guide
Log Descriptions
K-3
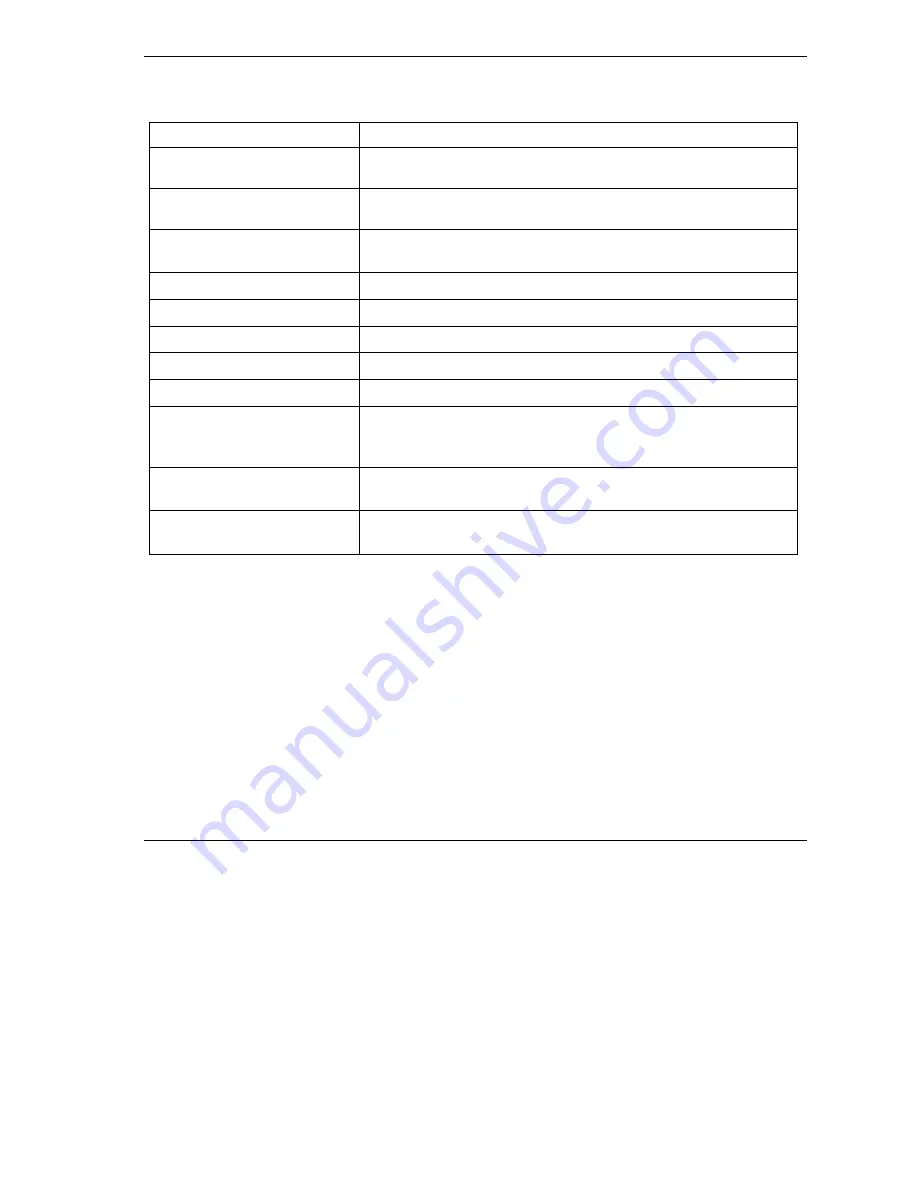
Chart K-4 Attack Logs
LOG MESSAGE
DESCRIPTION
attack (Protocol)
The firewall detected an attack. The log may also display the protocol
(for example TCP or UDP).
land Protocol)
The firewall detected a land attack. The log may also display the
protocol (for example TCP or UDP).
icmp echo ICMP
(type:%d, code:%d)
The firewall detected an ICMP echo attack. See the section on ICMP
messages for type and code details.
syn flood TCP
The firewall detected a TCP syn flood attack.
ports scan TCP
The firewall detected a TCP port scan attack.
teardrop (Protocol)
The firewall detected a teardrop attack.
illegal command TCP
The firewall detected a TCP SMTP illegal command attack.
NetBIOS TCP
The firewall detected a TCP NetBIOS attack.
ip spoofing - no
routing entry
(Protocol)
The firewall detected an IP spoofing attack while the Prestige did not
have a default route. The log may also display the protocol (for
example TCP or UDP).
vulnerability ICMP
(type:%d, code:%d)
The firewall detected an ICMP vulnerability attack; see the section on
ICMP messages for type and code details.
traceroute ICMP
(type:%d, code:%d)
The firewall detected an ICMP traceroute attack; see the section on
ICMP messages for type and code details.
Access logs may include the following information:
(Protocol) is the protocol of the packet (for example TCP or UDP) that triggered the log.
(Direction) is the direction in which the packet was traveling (for example LAN to WAN or WAN
to LAN)
(Rule) is the number of the firewall rule that caused the log.
Содержание Prestige 652H series
Страница 1: ...Prestige 652H HW Series ADSL Security Wireless LAN Router User s Guide Version 3 40 March 2004 ...
Страница 32: ......
Страница 50: ......
Страница 66: ......
Страница 68: ......
Страница 76: ......
Страница 80: ......
Страница 120: ...Prestige 652H HW Series User s Guide 8 12 WAN Setup Figure 8 6 Advanced WAN Backup ...
Страница 128: ......
Страница 146: ......
Страница 148: ......
Страница 162: ......
Страница 173: ...Prestige 652H HW Series User s Guide Firewall Screens 13 11 Figure 13 5 Insert Append A Firewall Rule ...
Страница 178: ...Prestige 652H HW Series User s Guide 13 16 Firewall Screens Figure 13 8 Rule Edit Example ...
Страница 196: ......
Страница 197: ...VPN IPSec V Part V VPN IPSec This part provides information about configuring VPN IPSec for secure communications ...
Страница 198: ......
Страница 204: ......
Страница 214: ...Prestige 652H HW Series User s Guide 16 10 VPN Screens Figure 16 5 VPN IKE ...
Страница 227: ...Prestige 652H HW Series User s Guide VPN Screens 16 23 Figure 16 8 Manual Setup ...
Страница 238: ......
Страница 258: ......
Страница 277: ...Maintenance VIII Part VIII Maintenance This part covers the maintenance screens ...
Страница 278: ......
Страница 296: ......
Страница 298: ......
Страница 308: ......
Страница 324: ......
Страница 330: ......
Страница 386: ......
Страница 406: ......
Страница 418: ......
Страница 428: ......
Страница 450: ......
Страница 454: ......
Страница 464: ......
Страница 470: ......
Страница 486: ......
Страница 493: ...XII Part XII Appendices and Index This part contains additional background information and an index or key terms ...
Страница 494: ......
Страница 500: ......
Страница 511: ...Prestige 652H HW Series User s Guide Wireless LAN and IEEE 802 11 C 3 Diagram C 2 ESS Provides Campus Wide Coverage ...
Страница 512: ......
Страница 516: ......
Страница 520: ......
Страница 560: ......
Страница 574: ......