Prestige 652H/HW Series User’s Guide
Firewall Screens
13-3
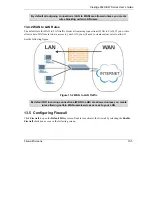
6. What computers on the Internet will be affected? The more specific, the better. For example, if traffic is
being allowed from the Internet to the LAN, it is better to allow only certain machines on the Internet to
access the LAN.
13.3.2 Security Ramifications
Once the logic of the rule has been defined, it is critical to consider the security ramifications created by the
rule:
1. Does this rule stop LAN users from accessing critical resources on the Internet? For example, if IRC is
blocked, are there users that require this service?
2. Is it possible to modify the rule to be more specific? For example, if IRC is blocked for all users, will a
rule that blocks just certain users be more effective?
3. Does a rule that allows Internet users access to resources on the LAN create a security vulnerability? For
example, if FTP ports (TCP 20, 21) are allowed from the Internet to the LAN, Internet users may be able
to connect to computers with running FTP servers.
4. Does this rule conflict with any existing rules?
Once these questions have been answered, adding rules is simply a matter of plugging the information into
the correct fields in the web configurator screens.
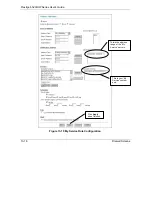
13.3.3 Key Fields For Configuring Rules
Action
Should the action be to
Block
or
Forward
?
“Block” means the firewall silently discards the packet.
Service
Select the service from the
Service
scrolling list box. If the service is not listed, it is necessary to first define
it. See
section 13.7
for more information on predefined services.
Source Address
What is the connection’s source address; is it on the LAN, DMZ or WAN? Is it a single IP, a range of IPs or
a subnet?
Содержание Prestige 652H series
Страница 1: ...Prestige 652H HW Series ADSL Security Wireless LAN Router User s Guide Version 3 40 March 2004 ...
Страница 32: ......
Страница 50: ......
Страница 66: ......
Страница 68: ......
Страница 76: ......
Страница 80: ......
Страница 120: ...Prestige 652H HW Series User s Guide 8 12 WAN Setup Figure 8 6 Advanced WAN Backup ...
Страница 128: ......
Страница 146: ......
Страница 148: ......
Страница 162: ......
Страница 173: ...Prestige 652H HW Series User s Guide Firewall Screens 13 11 Figure 13 5 Insert Append A Firewall Rule ...
Страница 178: ...Prestige 652H HW Series User s Guide 13 16 Firewall Screens Figure 13 8 Rule Edit Example ...
Страница 196: ......
Страница 197: ...VPN IPSec V Part V VPN IPSec This part provides information about configuring VPN IPSec for secure communications ...
Страница 198: ......
Страница 204: ......
Страница 214: ...Prestige 652H HW Series User s Guide 16 10 VPN Screens Figure 16 5 VPN IKE ...
Страница 227: ...Prestige 652H HW Series User s Guide VPN Screens 16 23 Figure 16 8 Manual Setup ...
Страница 238: ......
Страница 258: ......
Страница 277: ...Maintenance VIII Part VIII Maintenance This part covers the maintenance screens ...
Страница 278: ......
Страница 296: ......
Страница 298: ......
Страница 308: ......
Страница 324: ......
Страница 330: ......
Страница 386: ......
Страница 406: ......
Страница 418: ......
Страница 428: ......
Страница 450: ......
Страница 454: ......
Страница 464: ......
Страница 470: ......
Страница 486: ......
Страница 493: ...XII Part XII Appendices and Index This part contains additional background information and an index or key terms ...
Страница 494: ......
Страница 500: ......
Страница 511: ...Prestige 652H HW Series User s Guide Wireless LAN and IEEE 802 11 C 3 Diagram C 2 ESS Provides Campus Wide Coverage ...
Страница 512: ......
Страница 516: ......
Страница 520: ......
Страница 560: ......
Страница 574: ......