Application and functions
1.4 Security functions
TIM 1531 IRC
Operating Instructions, 02/2018, C79000-G8976-C468-02
19
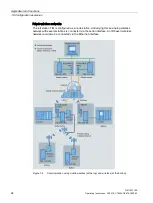
Additional protection be using security modules
With Industrial Ethernet Security, individual devices, automation cells or network segments
of an Ethernet network can be protected. The following security modules are suitable for
connecting the TIM to public networks:
●
SCALANCE M800
Routers for IP-based data transfer via DSL or mobile networks of the standards GPRS,
EGPRS, UMTS, LTE
●
SCALANCE S
Security modules for connection to Ethernet networks
The data transfer of the TIM along with a security module can be protected from the
following attacks by a combination of different security measures:
●
Data espionage
●
Data manipulation
●
Unwanted access
Secure underlying networks can be operated via additional Ethernet interfaces of the TIM or
CPU.
Using the security modules mentioned above SCALANCE M / SCALANCE S the following
additional security functions can be used:
●
Firewall
–
IP firewall with stateful packet inspection (layer 3 and 4)
–
Firewall also for "non-IP" Ethernet frames according to IEEE 802.3 (layer 2)
–
Limitation of the transmission speed to restrict flooding and DoS attacks ("Define IP
packet filter rules")
–
Global firewall rule sets
●
Protection for devices and network segments
The protection provided by the firewall can cover individual devices, several devices or
even entire network segments.
●
Communication made secure by IPsec tunnels (VPN)
VPN tunnel communication allows the establishment of secure IPsec tunnels for
communication with one or more security modules.
VPN can be used for communication via mobile wireless and the Internet (DSL) along
with a SCALANCE M router. The SCALANCE M800 product line includes various VPN
routers with encryption software and a firewall.
The router can be put together with other modules to form VPN groups during
configuration. IPsec tunnels (VPN) are created between all security modules of a VPN
group. All internal nodes of these security modules can communicate securely with each
other through these tunnels.
●
Logging
To allow monitoring, events can be stored in log files that can be read out using the
configuration tool or can be sent automatically to a Syslog server.
Содержание TIM 1531 IRC
Страница 262: ...Block library TeleControl ST7 5 7 Master copies TIM 1531 IRC 262 Operating Instructions 02 2018 C79000 G8976 C468 02 ...
Страница 302: ...Dimension drawings TIM 1531 IRC 302 Operating Instructions 02 2018 C79000 G8976 C468 02 ...
Страница 322: ...Documentation references 13 TIM 1531 IRC 322 Operating Instructions 02 2018 C79000 G8976 C468 02 ...
Страница 336: ...Glossary TIM 1531 IRC 336 Operating Instructions 02 2018 C79000 G8976 C468 02 ...