170
Glossary
E
Encryption
Changing data into a form that cannot be understood by others. A rule (algorithm) and a key
(network key) for converting data between a sender and a receiver are determined, and the
data converted (encrypted) by the sender is returned to its original form (decrypted) by the
receiver. In this way, important interactions cannot be deciphered by others.
ESS-ID
– Extended Service Set ID
A text string that identifies the sender when using wireless LAN. Since communications use
wireless LAN radio waves, data can be exchanged with a large number of networks. Each
computer or access point (
) confirms this text string, allowing communications only
between parties with matching ESS-IDs.
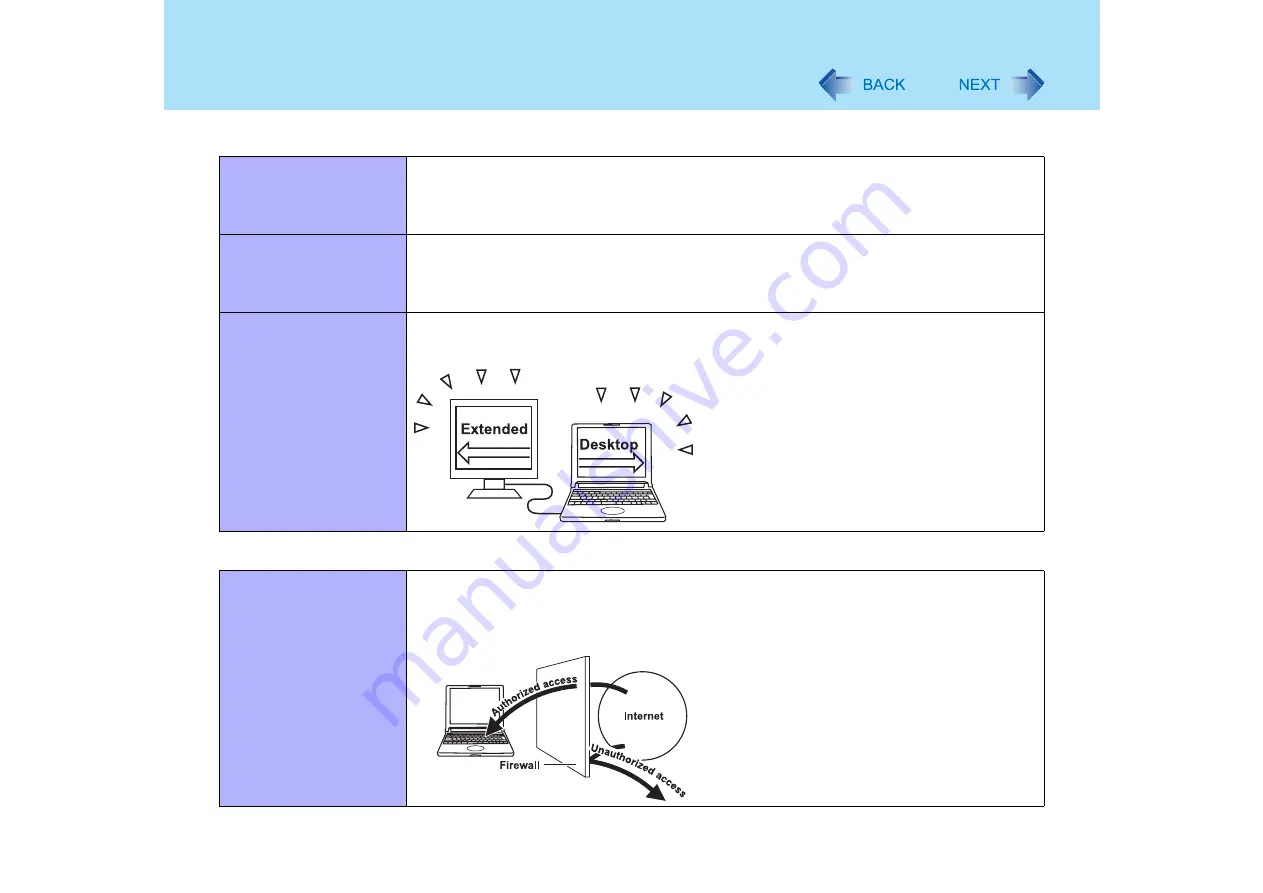
Extended Desktop (Dual
Display)
Using the internal LCD (
) and an external display as a continuous display field.
Windows and other items can be dragged between the two displays.
F
Firewall
A security system for protecting the computer from unauthorized access via the Internet or
other external networks. The firewall regulates the data exchanged between the computer and
the external network, so that only approved data can pass through.
z
Windows Firewall is provided in Windows XP.













































