Chapter 6 – RouteFinder Software
Multi-Tech Systems, Inc. RouteFinderVPN RF760/660/600VPN User Guide (PN S000323D)
60
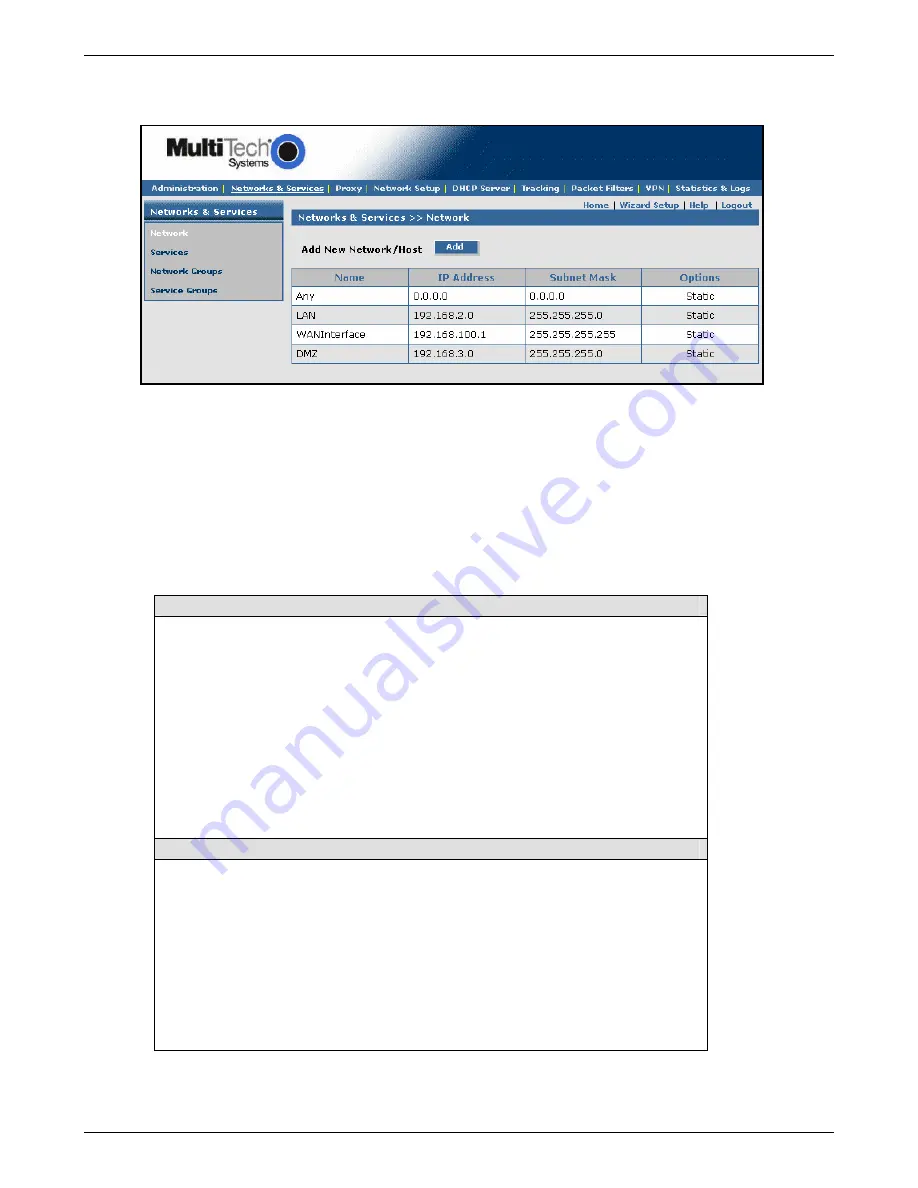
Networks & Services > Networks
After clicking the
Add
button, the Networks you have setup display on the lower part of the screen.
Example 1 – After the networks in the example are added, you will see the following entries added to the
table on this screen:
Name IP
Address
Subnet
Mask Options
RemoteLAN
192.168.100
255.255.255.0
Edit | Delete
RemoteWAN_IP
204.26.122.3
255.255.255.255
Edit | Delete
Notes:
•
The first four networks on this screen are default entries and cannot be changed.
•
Networks added using the
Add Network/Host
function on this screen will also display in the
Remote Gateway IP
and
Remote LAN
dropdown boxes on the
VPN > IPSec > IKE
screen.
Entries on This Screen Affect Other Screens
Networks added on this screen will display on the following screens:
Administration Access
Network Groups
SSH
Packet Filter Rules
Network Intrusion Detection
Routing
Masquerading
SNAT
DNAT
HTTP Proxy
SMTP Proxy
DNS Proxy
IPSec
PPTP
Network Names added on this screen will be made available to:
Add Allowed Networks
on Administration Access screen
Add packet filter rules
Add source
for Destination Networks on the Network Intrusion Detection screen
Add Routes
on the Routing screen
SNAT
Masquerading
Port scan detection and DNAT sections
Add allowed networks
on SSH, HTTP Proxy, and DNS Proxy screens
Add relay networks
on SMTP Proxy screen
Add subnets
on IPSec screen
Add local and remote IP addresses
on PPTP screen
Mac address filtering (destination IP address)
on the Packet Filters > Advanced screen






























