xStack
®
DGS-3600 Series Layer 3 Managed Gigabit Ethernet Switch
Appendix F
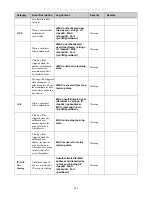
RADIUS Attributes Assignment
The RADIUS Attributes Assignment on the Switch is used in the following modules: 802.1X (Port-based and MAC-based), Web-
based Access Control (WAC), Japanese Web-based Access Control (JWAC), and MAC-based Access Control.
The description that follows explains the following RADIUS Attributes Assignment types:
Ingress/Egress Bandwidth
802.1p Default Priority
VLAN
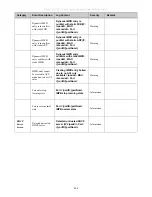
To assign Ingress/Egress bandwidth by RADIUS Server, the proper parameters should be configured on the RADIUS Server. The
tables below show the parameters for bandwidth.
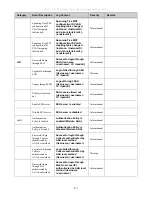
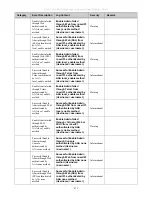
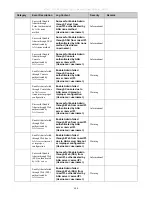
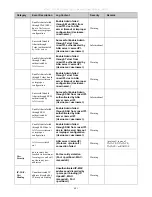
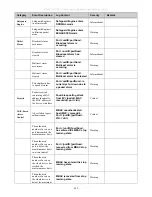
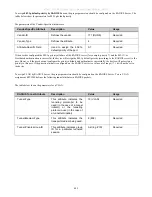
The parameters of the Vendor-Specific attributes are:
Vendor-Specific Attribute
Description
Value
Usage
Vendor-ID
Defines the vendor.
171 (DLINK)
Required
Vendor-Type
Defines the attribute.
2
(for
ingress
bandwidth)
3 (for egress
bandwidth)
Required
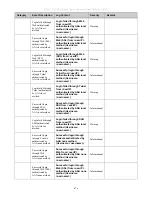
Attribute-Specific Field
Used to assign the bandwidth
of a port.
Unit (Kbits)
Required
If the user has configured the bandwidth attribute of the RADIUS server (for example, ingress bandwidth 1000Kbps) and the
802.1X authentication is successful, the device will assign the bandwidth (according to the RADIUS server) to the port. However,
if the user does not configure the bandwidth attribute and authenticates successfully, the device will not assign any bandwidth to
the port. If the bandwidth attribute is configured on the RADIUS server with a value of “0” or more, than the effective bandwidth
(100Mbps on an Ethernet port or 1Gbps on a Gigabit port) of the port will be set to
no_limited
.
488