4. CONFIGURATION
Continued from previous page
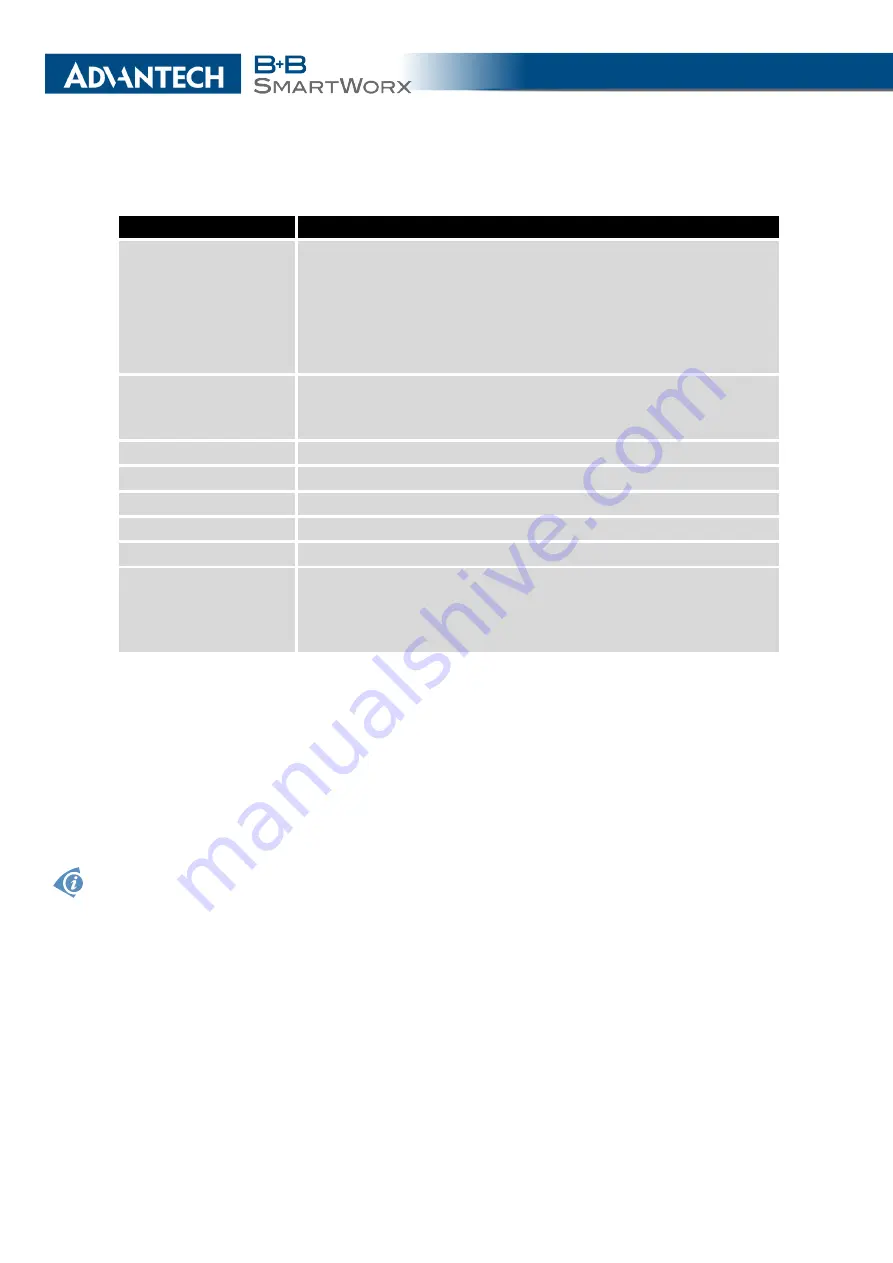
Item
Description
Authenticate Mode
Specifies the means by which the router authenticates:
•
Pre-shared key
– Sets the shared key for both sides of the
tunnel.
•
X.509 Certificate
– Allows X.509 authentication in multi-
client mode.
Pre-shared Key
Specifies the shared key for both sides of the tunnel. The prereq-
uisite for entering a key is that you select pre-shared key as the
authentication mode.
CA Certificate
Certificate for X.509 authentication.
Remote Certificate
Certificate for X.509 authentication.
Local Certificate
Certificate for X.509 authentication.
Local Private Key
Private key for X.509 authentication.
Local Passphrase
Passphrase used during private key generation.
Debug
Choose the level of verbosity to System Log. Silent (default),
audit, control, control-more, raw, private (most verbose includ-
ing the private keys). See strongSwan documentation for more
details.
Table 42: IPsec Tunnel Configuration
The IPsec function supports the following types of identifiers (ID) for both sides of the
tunnel,
Remote ID
and
Local ID
parameters:
•
IP address (for example, 192.168.1.1)
•
DN (for example, C=CZ,O=CompanyName,OU=TP,CN=A)
•
FQDN (for example, @director.companyname.cz) –
the @ symbol proceeds the FQDN.
•
User FQDN (for example, [email protected])
The certificates and private keys have to be in the PEM format. Use only certificates containing
start and stop tags.
The random time, after which the router re-exchanges new keys is defined as follows:
Lifetime - (Rekey random value in range (from 0 to Rekey margin * Rekey Fuzz/100))
The default exchange of keys is in the following time range:
•
Minimal time: 1h - (9m + 9m) = 42m
•
Maximal time: 1h - (9m + 0m) = 51m
75
Summary of Contents for SmartMotion
Page 1: ...Twin Cellular Module Router SmartMotion CONFIGURATION MANUAL ...
Page 24: ...3 STATUS WiFi Scan output may look like this Figure 4 WiFi Scan 14 ...
Page 27: ...3 STATUS Figure 5 Network Status 17 ...
Page 44: ...4 CONFIGURATION Figure 24 1st Mobile WAN Configuration 34 ...
Page 62: ...4 CONFIGURATION Figure 31 WiFi Configuration 52 ...
Page 86: ...4 CONFIGURATION Figure 46 IPsec Tunnels Configuration 76 ...
Page 112: ...4 CONFIGURATION Figure 67 Example 2 USB port configuration 102 ...
















































