Chapter 21 IPSec VPN
USG20(W)-VPN Series User’s Guide
341
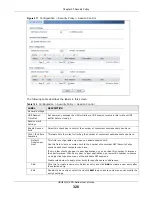
Each field is described in the following table.
Table 135
Configuration > VPN > IPSec VPN > VPN Connection > Edit
LABEL
DESCRIPTION
Show Advanced
Settings / Hide
Advanced Settings
Click this button to display a greater or lesser number of configuration fields.
Create new Object
Use to configure any new settings objects that you need to use in this screen.
General Settings
Enable
Select this check box to activate this VPN connection.
Connection Name
Type the name used to identify this IPSec SA. You may use 1-31 alphanumeric
characters, underscores (
_
), or dashes (-), but the first character cannot be a
number. This value is case-sensitive.
Nailed-Up
Select this if you want the USG to automatically renegotiate the IPSec SA when the
SA life time expires.
Enable Replay
Detection
Select this check box to detect and reject old or duplicate packets to protect against
Denial-of-Service attacks.
Enable NetBIOS
Broadcast over
IPSec
Select this check box if you the USG to send NetBIOS (Network Basic Input/Output
System) packets through the IPSec SA.
NetBIOS packets are TCP or UDP packets that enable a computer to connect to and
communicate with a LAN. It may sometimes be necessary to allow NetBIOS packets
to pass through IPSec SAs in order to allow local computers to find computers on the
remote network and vice versa.
MSS Adjustment
Select
Custom Size
to set a specific number of bytes for the Maximum Segment Size
(MSS) meaning the largest amount of data in a single TCP segment or IP datagram
for this VPN connection.
Some VPN clients may not be able to use a custom MSS size if it is set too small. In
that case those VPN clients will ignore the size set here and use the minimum size
that they can use.
Select
Auto
to have the USG automatically set the MSS for this VPN connection.
Narrowed
If the IP range on the USG (local policy) and the local IP range on the remote IPSec
router overlap in an IKEv2 SA, then you may select
Narrowed
to have the SA only
apply to the IP addresses in common.
Here are some examples.
USG (local policy) Remote IPSec router
IKEv2 SA-1 192.168.20.0/24 192.168.20.1 ~ 192.168.20.20
Narrowed 192.168.20.1 ~ 192.168.20.20
IKEv2 SA- 2 192.168.30.50 ~ 192.168.30.70 192.168.30.60 ~ 192.168.30.80
Narrowed 192.168.30.60 ~ 192.168.30.70
VPN Gateway
Application
Scenario
Select the scenario that best describes your intended VPN connection.
Site-to-site
- Choose this if the remote IPSec router has a static IP address or a
domain name. This USG can initiate the VPN tunnel.
Site-to-site with Dynamic Peer
- Choose this if the remote IPSec router has a
dynamic IP address. Only the remote IPSec router can initiate the VPN tunnel.
Remote Access (Server Role)
- Choose this to allow incoming connections from
IPSec VPN clients. The clients have dynamic IP addresses and are also known as dial-
in users. Only the clients can initiate the VPN tunnel.
Remote Access (Client Role)
- Choose this to connect to an IPSec server. This USG
is the client (dial-in user) and can initiate the VPN tunnel.
Summary of Contents for ZyWall USG20-VPN
Page 17: ...17 PART I User s Guide ...
Page 18: ...18 ...
Page 99: ...99 PART II Technical Reference ...
Page 100: ...100 ...