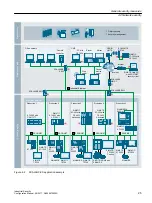
Possible security holes or weak points
The security chain of a company is only as strong as its weakest link. Security holes can exist
at numerous points. The following list gives only a few examples:
● Employees / external companies
● Production plants
● Network infrastructure
● Data centers / PC workstations
● Laptops/tablets
● Printers
● Smartphones/smartwatches
● Mobile data storage media
For this reason, a holistic approach is required to deal with the issue of security. Coordinated
guidelines and regulations are required that cover all areas: Devices, systems, processes and
employees.
The topic of data security and access protection (security) is becoming more and more
important in industrial environments. The following technologies results in higher requirements
placed on protecting and securing industrial plants and systems:
● The ongoing networking of complete industrial plants and systems
● The vertical integration and networking of various company levels
● New techniques, e.g. remote maintenance and/or remote access
The threats are diverse and the consequences are far-reaching:
Possible threats:
Potential threats come from the industry environment and involve the topic of confidentiality,
integrity and availability. Examples of threats include the following:
● Espionage of data, recipes, etc.
● Sabotage of production plants
● System stoppage, e.g. due to virus infection and malware
● Manipulation of data or application software
● Unauthorized use of system functions
Possible effects of a security incident
● Loss of intellectual property
● Loss of production or reduced product quality
● Negative company image and economic damage
● Catastrophic environmental influences
● Danger to people and machines
Industrial Security
3.3 Why is Industrial Security so important?
Industrial Security
Configuration Manual, 08/2017, A5E36912609A
13