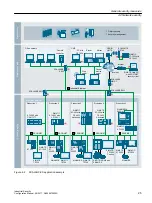
Separation via a DMZ network
In the more secure variant, the coupling is established via a separate DMZ (demilitarized zone)
network. In this case, direct communication between the production network and the company
network is completely prevented by firewalls and only takes place indirectly via servers in the
DMZ network.
Note
The production networks should also be divided into separate automation cells in order to
protect critical communication mechanisms.
General security measures
Adhere to the general security measures even within protection zones, e.g. the use of a virus
scanner (Page 28) or the reduction of points of attack.
See also
Reduction of attack points (Page 26)
4.2.1.2
Network segmentation with SCALANCE S
Siemens provides SCALANCE S security modules to meet network protection and network
segmentation requirements. Further information on SIEMENS SCALANCE S can be found on
http://w3.siemens.com/mcms/industrial-communication/en/ie/industrial-ethernet-
security/scalance-s/Pages/default.aspx
SCALANCE S security module
SCALANCE S security modules with Security Integrated provide:
● Stateful inspection firewall
In order to implement user-specific control and logging, firewall rules can also be specified
that only apply to certain users.
● VPN via IPsec (data encryption and authentication)
This establishes a secure tunnel between authenticated users whose data cannot be
intercepted or manipulated. The most important aspect is the protection against external
access via the Internet.
● NAT/NATP (address translation)
● Router functionality (PPPoE, DDNS) for broadband Internet access (DSL, cable)
● SCALANCE S623 with additional VPN port (DMZ) enables the secure connection of an
additional network for service and remote maintenance purposes. S623 also permits the
secure, redundant connection of subordinate networks by means of routers and firewall
redundancy.
● SCALANCE S615 has five Ethernet ports with which different network topologies can be
protected by means of a firewall or Virtual Private Network VPN (IPsec and OpenVPN),
and security concepts implemented flexibly.
General security measures
4.2 Network security
Industrial Security
22
Configuration Manual, 08/2017, A5E36912609A