66&
6HFXULW\PDQDJHPHQW
2EMHFWVHFXULW\
3URGXFWLRQ
3URGXFWLRQ
3URGXFWLRQ
6,027,21'[ZLWK
6,1$0,&6
6,0$7,&
6ZLWK
&3
$GYDQFHG
6,0$7,&ILHOG3*
ZLWK62)71(7
VHFXULW\FOLHQW
3&ZLWK
&3
&HQWUDO
DUFKLYH
VHUYHU
3O
DQ
WVH
FX
ULW
\
6\VW
HP
LQ
WH
JUL
W\
1
HW
Z
RUN
VH
FX
ULW
\
3URGXFWLRQQHWZRUN
2IILFHQHWZRUN
6,0$7,&
6ZLWK
&3
3URGXFWLRQ
3URGXFWLRQ
6,0$7,&
6ZLWK
&3
$GYDQFHG
6ZLWK
&60
6,0$7,&
6ZLWK
&3
:HE
VHUYHU
6HUYHU
*356
8076
,QWHUQHW
'0=
,QGXVWULDO(WKHUQHW
6HUYHU
'RPDLQ
FRQWUROOHU
,QWHUQHW
URXWHU
6,0$7,&
73
&RPIRUW
6,0$7,&
(76
6,1$0,&6
6,0$7,&
.73
6,0$7,&
(7
63
6,1$0,&6 6,0$7,&
73
6,0$7,&
(7
63
6,1$0,&6 6,0$7,&
73
(7
6,0$7,&
73
6,0$7,&
6
6,180(5,.
'VO
6,0$7,&
6
352),1(7
352),1(7
352),1(7
352),1(7
352),1(7
6&$/$1&(6
6&$/$1&(6
6&$/$1&(
6
6&$/$1&(
0
6&$/$1&(
0
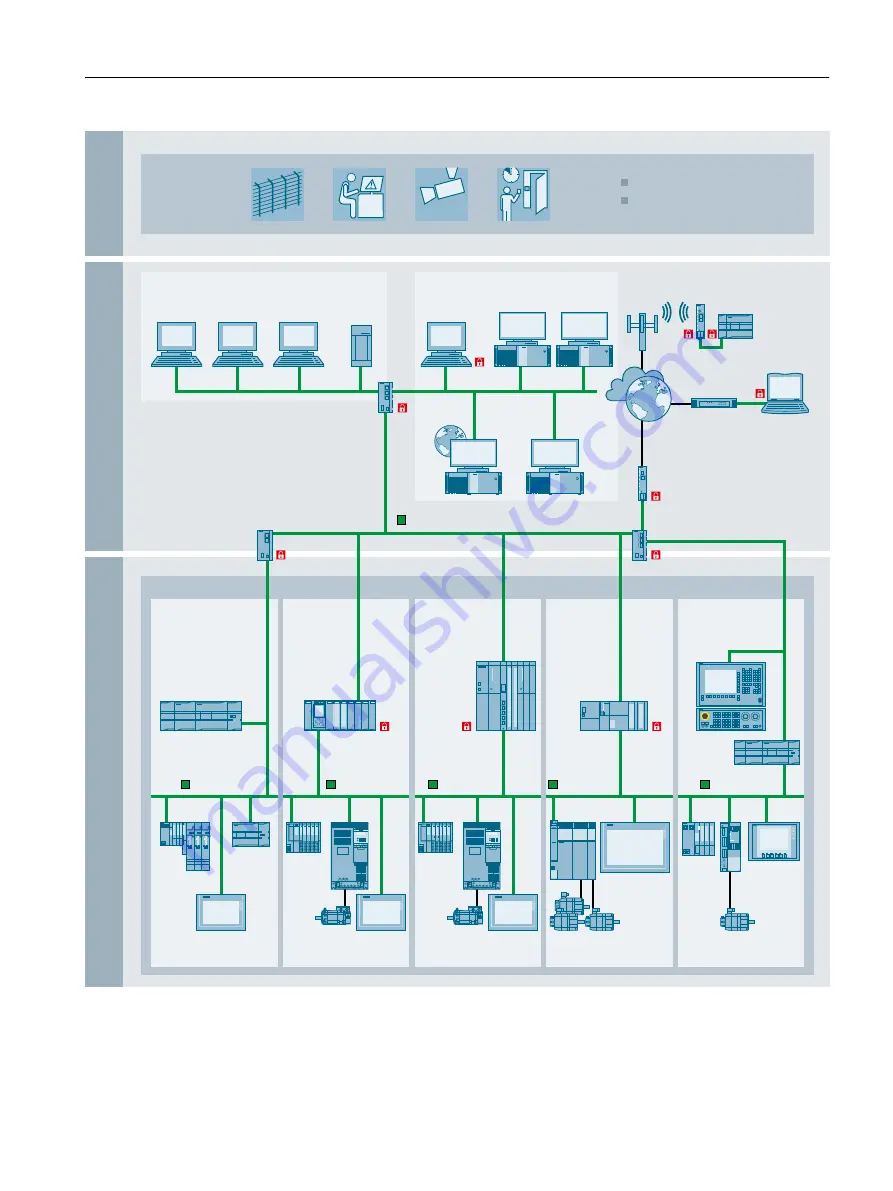
Figure 4-2
SCALANCE S application example
General security measures
4.2 Network security
Industrial Security
Configuration Manual, 08/2017, A5E36912609A
25