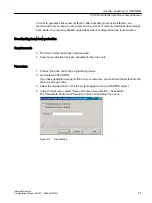
Assigning secure passwords
Observe the following rules when assigning new passwords:
● Never assign passwords that can be easily guessed, e.g. simple words, simple key
combinations on the keyboard, etc.
● Passwords must comprise at least eight characters.
● PINS must comprise an arbitrary sequence of digits.
● Passwords must always contain a combination of upper-case and lower-case letters as
well as numbers and special characters.
● Wherever possible and where it is supported by the IT systems and the software, a
password must always have a character sequence as complex as possible.
Note
The German Federal Office for IT Security (BSI) (
https://www.bsi.bund.de/EN/Topics/
ITGrundschutz/ITGrundschutzCatalogues/itgrundschutzcatalogues_node.html
) provides
additional rules for creating secure passwords
Programs are available that can help you to manage your passwords. Using these programs,
you can encrypt, save and manage your passwords and secret numbers – and also create
secure passwords.
Product security notifications
Threats are extremely diverse in nature and are continually changing. Always keep yourself
up-to-date on a regular basis through the Industry Online Support (Page 223) regarding
whether there are new and relevant product security notifications for your particular products.
Comply with the instructions provided in the product security notifications.
4.3.1.2
Virus scanner
An anti-virus program, virus scanner or virus protection program is a software that can detect,
block and, if required, eliminate computer viruses, computer worms or Trojans.
In principle, virus scanners can only detect known malware, e.g. viruses, worms, Trojans, etc.,
or harmful logic. Therefore, virus scanners cannot provide protection against all viruses or
worms. For this reason, virus scanners can only be considered as a complement to general
precautionary measures.
The use of a virus scanner must not impact the production operations of a plant. As the last
consequence, this will lead to even a virus-infected computer not being permitted to
immediately shut down if this would cause the control of the production process to be lost.
General security measures
4.3 System integrity
Industrial Security
28
Configuration Manual, 08/2017, A5E36912609A