1-13
Firepower 7000 and 8000 Series Installation Guide
Chapter 1 Introduction to the Firepower System
Security, Internet Access, and Communication Ports
Security, Internet Access, and Communication Ports
To safeguard the Firepower Management Center, you should install it on a protected internal network.
Although the Firepower Management Center is configured to have only the necessary services and ports
available, you must make sure that attacks cannot reach it (or any managed devices) from outside the
firewall.
If the Firepower Management Center and its managed devices reside on the same network, you can
connect the management interfaces on the devices to the same protected internal network as the
Firepower Management Center. This allows you to securely control the devices from the Firepower
Management Center. You can also configure multiple management interfaces to allow the Firepower
Management Center to manage and isolate traffic from devices on other networks.
Regardless of how you deploy your appliances, intra-appliance communication is encrypted. However,
you must still take steps to ensure that communications between appliances cannot be interrupted,
blocked, or tampered with; for example, with a distributed denial of service (DDoS) or
man-in-the-middle attack.
Also note that specific features of the Firepower System require an Internet connection. By default, all
appliances are configured to directly connect to the Internet. Additionally, the system requires certain
ports remain open for basic intra-appliance communication, for secure appliance access, and so that
specific system features can access the local or Internet resources they need to operate correctly.
Tip
With the exception of Cisco ASA with FirePOWER Services, Firepower System appliances support the
use of a proxy server. For more information, see the
Firepower Management Center Configuration
Guide
.
For more information, see:
•
Internet Access Requirements, page 1-13
•
Communication Ports Requirements, page 1-14
Internet Access Requirements
Firepower System appliances are configured to directly connect to the Internet on ports 443/tcp (HTTPS)
and 80/tcp (HTTP), which are open by default; see
Communication Ports Requirements, page 1-14
that most Firepower System appliances support use of a proxy server; see the Configuring Network
Settings chapter in the
Firepower Management Center Configuration Guide
. Note also that a proxy
server cannot be used for whois access.
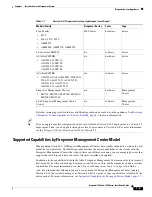
The following table describes the Internet access requirements of specific features of the Firepower
System.
Table 1-6
Firepower System Feature Internet Access Requirements
Feature
Internet access is required to...
Appliances
dynamic analysis: querying
query the Collective Security Intelligence
Cloud for threat scores of files previously
submitted for dynamic analysis.
Management Center
dynamic analysis: submitting
submit files to the Collective Security
Intelligence Cloud for dynamic analysis.
Managed devices