3-8
Firepower 7000 and 8000 Series Installation Guide
Chapter 3 Deploying Firepower Managed Devices
Deployment Options
Figure 3-2
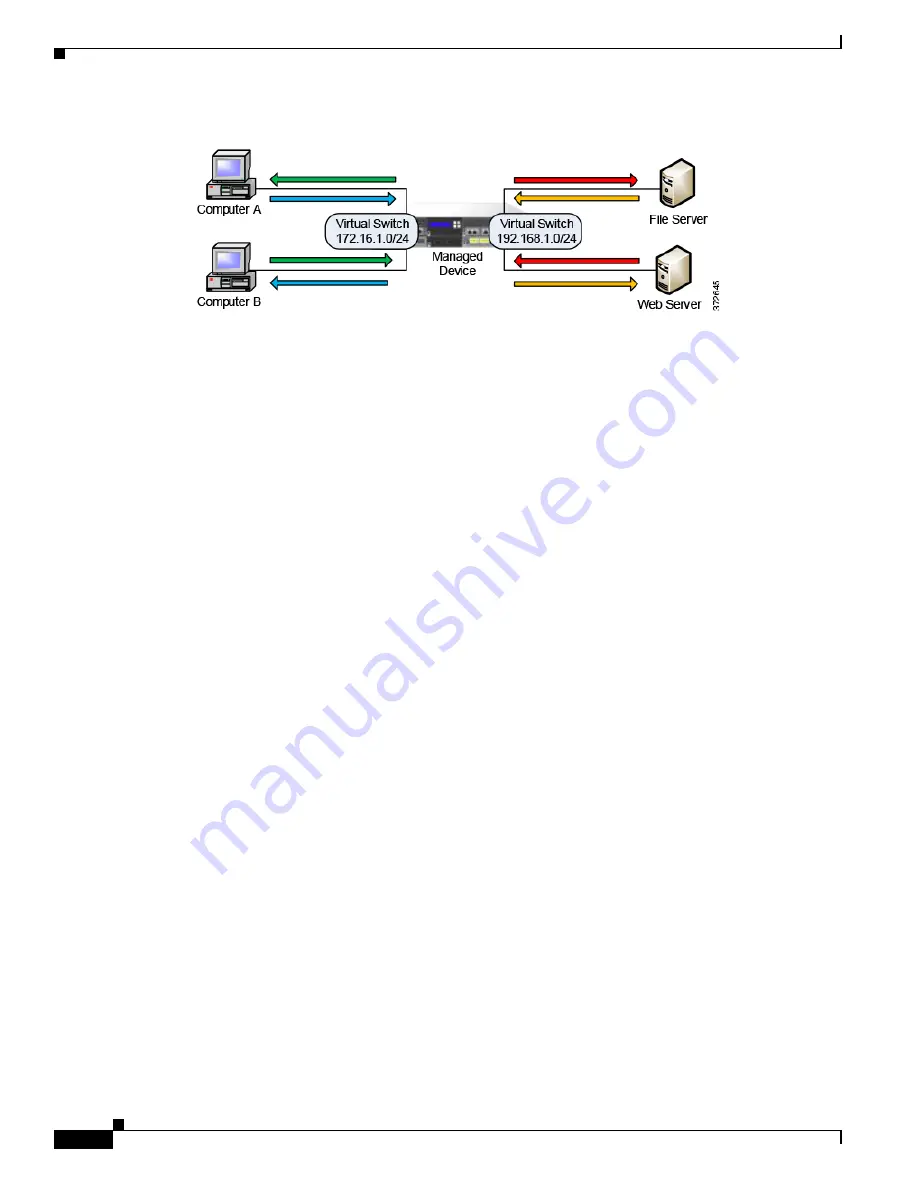
Virtual Switches on a Managed Device
In this example, the managed device monitors traffic from two separate networks, 172.16.1.0/20 and
192.168.1.0/24. Although both networks are monitored by the same managed device, the virtual switch
passes traffic only to those computers or servers on the same network. Traffic can pass from computer
A to computer B through the 172.16.1.0/24 virtual switch (indicated by the blue line) and from computer
B to computer A through the same virtual switch (indicated by the green line). Similarly, traffic can pass
to and from the file and web servers through the 192.168.1.0/24 virtual switch (indicated by the red and
orange lines). However, traffic cannot pass between the computers and the web or file servers because
the computers are not on the same virtual switch as the servers.
For more information on configuring switched interfaces and virtual switches, see Setting Up Virtual
Switches in the
Firepower Management Center Configuration Guide.
Deploying with a Virtual Router
You can create a
virtual router
on a managed device to route traffic between two or more networks, or
to connect a private network to a public network (for example, the Internet). The virtual router connects
two routed interfaces to provide Layer 3 packet forwarding decisions for your deployment according to
the destination address. Optionally, you can enable strict TCP enforcement on the virtual router. For
more information on routed interfaces, see
. You must use a virtual router
with a gateway VPN. For more information, see
Deploying a Gateway VPN, page 3-10
A virtual router can contain either physical or logical routed configurations from one or more individual
devices within the same broadcast domain. You must associate each logical interface with a VLAN tag
to handle traffic received by the physical interface with that specific tag. You must assign a logical routed
interface to a virtual router to route traffic.
To configure a virtual router, you set up routed interfaces with either physical or logical configurations.
You can configure physical routed interfaces for handling untagged VLAN traffic. You can also create
logical routed interfaces for handling traffic with designated VLAN tags. The system drops any traffic
received on an external physical interface that does not have a routed interface waiting for it. If the
system receives a packet with no VLAN tag and you have not configured a physical routed interface for
that port, it drops the packet. If the system receives a VLAN-tagged packet and you have not configured
a logical routed interface, it also drops the packet.
Virtual routers have the advantage of scalability. Where physical routers limit the number of networks
you can connect, multiple virtual routers can be configured on the same managed device. Putting
multiple routers on the same device reduces the physical complexity of your deployment, allowing you
to monitor and manage multiple routers from one device.
Use a virtual router where you would use a Layer 3 physical router to forward traffic between multiple
networks in your deployment, or to connect your private network to a public network. Virtual routers are
particularly effective in large deployments where you have many networks or network segments with
different security requirements.