CHAPTER 16 Services
Mediant 4000 SBC | User's Manual
●
In the 'RADIUS Packets Retransmission' field (RADIUSRetransmission), enter the
maximum number of RADIUS retransmissions that the device performs if no response is
received from the RADIUS server.
●
In the 'RADIUS Response Time Out' field (RadiusTO), enter the interval (in seconds) that
the device waits for a response before sending a RADIUS retransmission.
3.
Click
Apply
.
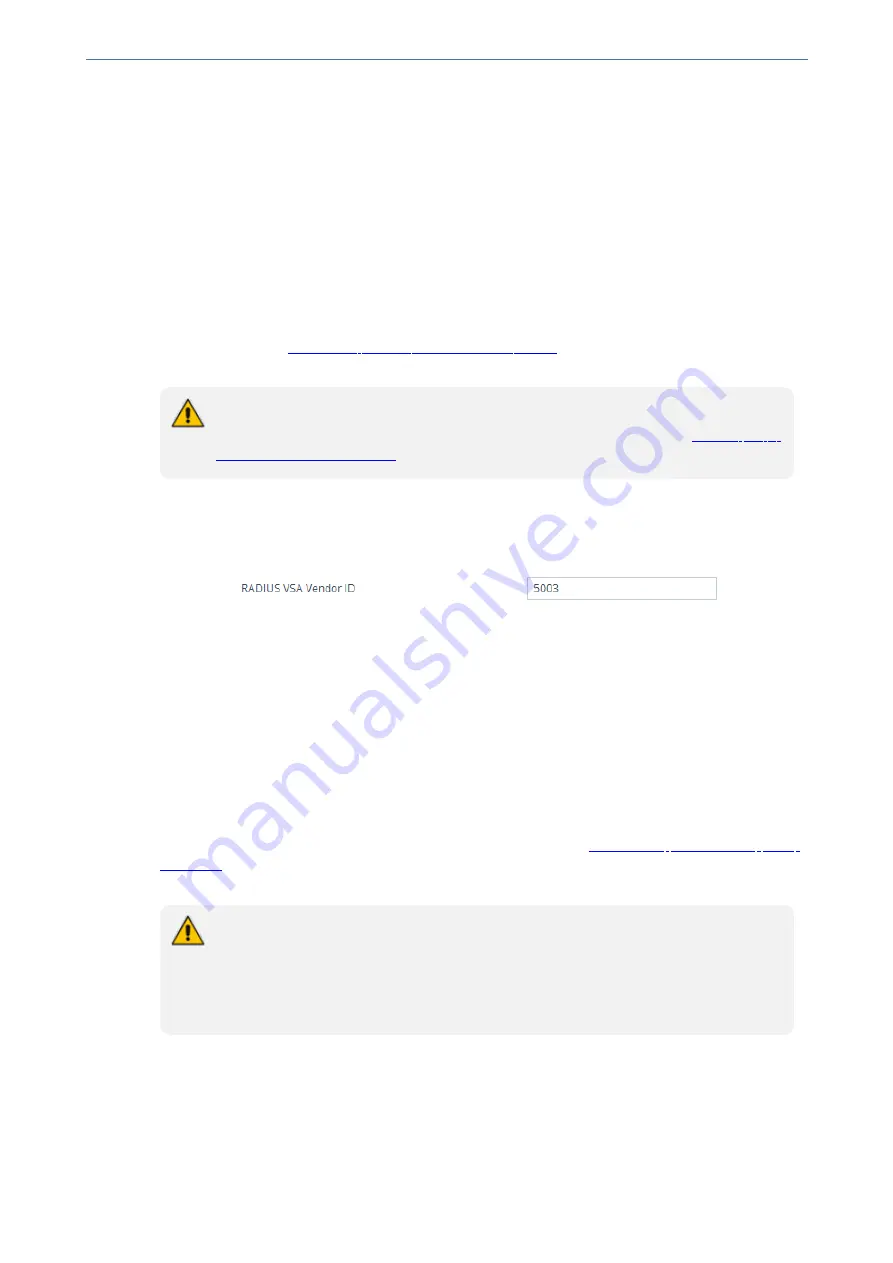
Configuring the RADIUS Vendor ID
The vendor-specific attribute (VSA) identifies the device to the RADIUS server using the Vendor ID
(as registered with the Internet Assigned Numbers Authority or IANA). The device's default vendor
ID is 5003 which can be changed, as described in the following procedure. For an example of using
the Vendor ID, see
Setting Up a Third-Party RADIUS Server
. The procedure is applicable to both
RADIUS-based user authentication and RADIUS-based accounting.
The Vendor ID must be the same as the Vendor ID set on the third-party RADIUS
server. See the example for setting up a third-party RADIUS server in
.
➢
To configure the RADIUS Vendor ID:
1.
Open the Authentication Server page (
Setup
menu >
Administration
tab >
Web & CLI
folder
>
Authentication Server
).
2.
Under the RADIUS group, in the 'RADIUS VSA Vendor ID' field, enter the
same
vendor ID
number as set on the third-party RADIUS server.
3.
Click
Apply
.
RADIUS-based Management User Authentication
You can enhance security for your device by implementing Remote Authentication Dial-In User
Service (RADIUS - RFC 2865) for authenticating multiple management user accounts of the
device’s embedded Web and Telnet (CLI) servers. Thus, RADIUS also prevents unauthorized
access to your device.
When RADIUS authentication is not used, the user's login username and password are locally
authenticated by the device using the Local Users table (see
). However, you can configure the device to use the Local Users table as a fallback
mechanism if the RADIUS server does not respond.
If you enable RADIUS- based user login authentication, when users with Security
Administrator privilege level log in to the device’s CLI, they are automatically given
access to the CLI privileged mode (“#”). For all other user privilege levels, the user
needs to run the
enable
command and then enter the password to access the CLI
privileged mode.
- 211 -
Содержание Mediant 4000 SBC
Страница 1: ...User s Manual AudioCodes Series of Session Border Controllers SBC Mediant 4000 SBC Version 7 2...
Страница 40: ...Part I Getting Started with Initial Connectivity...
Страница 48: ...Part II Management Tools...
Страница 113: ...Part III General System Settings...
Страница 118: ...Part IV General VoIP Configuration...
Страница 525: ...Part V Session Border Controller Application...
Страница 654: ...Part VI Cloud Resilience Package...
Страница 663: ...Part VII High Availability System...
Страница 685: ...Part VIII Maintenance...
Страница 759: ...Part IX Status Performance Monitoring and Reporting...
Страница 844: ...Part X Diagnostics...
Страница 888: ...Part XI Appendix...
Страница 1036: ...This page is intentionally left blank CHAPTER 62 Technical Specifications Mediant 4000 SBC User s Manual 1003...






























