906
Appendix H Software licensing information
320818-A
conditions apply to all code found in this distribution, be it the RC4, RSA, lhash, DES, etc., code; not just the SSL code.
The SSL documentation included with this distribution is covered by the same copyright terms except that the holder is
Tim Hudson ([email protected]). Copyright remains Eric Young's, and as such, any Copyright notices in the code are
not to be removed. If this package is used in a product, Eric Young should be given attribution as the author of the parts
of the library used. This can be in the form of a textual message at program start-up or in documentation (online or
textual) provided with the package. Redistribution and use in source and binary forms, with or without modification, are
permitted, provided that the following conditions are met:
1. Redistributions of source code must retain the copyright notice, this list of conditions, and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions, and the following
disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must display the following acknowledgement:
“This product includes cryptographic software written by Eric Young ([email protected])”. The word “cryptographic”
can be left out if the routines from the library being used are not cryptographic related.
4. If you include any Windows specific code (or a derivative thereof) from the apps directory (application code), you
must include an acknowledgement: “This product includes software written by Tim Hudson ([email protected])”.
THIS SOFTWARE IS PROVIDED BY ERIC YOUNG “AS IS” AND ANY EXPRESS OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS
FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR
CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE
GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
The licence and distribution terms for any publicly available version or derivative of this code cannot be changed. That
is, this code cannot simply be copied and put under another distribution licence [including the GNU Public Licence.]
GNU General Public License
Version 2, June 1991
Copyright © 1989, 1991 Free Software Foundation, Inc. 59 Temple Place, Suite 330, Boston, MA 02111-1307 USA
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed.
GNU GENERAL PUBLIC LICENSE
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
0. This License applies to any program or other work that contains a notice placed by the copyright holder saying it may
be distributed under the terms of this General Public License. The “Program,” below, refers to any such program or
work. A “work based on the Program” means either the Program or any derivative work under copyright law: that is, a
work containing the Program or a portion of it, either verbatim or with modifications and/or translated into another
language. (Hereinafter, translation is included without limitation in the term “modification.”) Each licensee is addressed
as “you.”
Activities other than copying, distribution and modification are not covered by this License; they are outside its scope.
The act of running the Program is not restricted, and the output from the Program is covered only if its contents
constitute a work based on the Program (independent of having been made by running the Program). Whether that is true
depends on what the Program does.
1. You may copy and distribute verbatim copies of the Program's source code as you receive it, in any medium, provided
that you conspicuously and appropriately publish on each copy an appropriate copyright notice and disclaimer of
Summary of Contents for 4050
Page 24: ...24 Contents 320818 A ...
Page 48: ...48 Chapter 1 Overview 320818 A ...
Page 70: ...70 Chapter 2 Initial setup 320818 A ...
Page 190: ...190 Chapter 4 Configuring the domain 320818 A ...
Page 232: ...232 Chapter 5 Configuring groups and profiles 320818 A ...
Page 352: ...352 Chapter 7 TunnelGuard SRS Builder 320818 A ...
Page 456: ...456 Chapter 9 Customizing the portal and user logon 320818 A ...
Page 568: ...568 Chapter 10 Configuring system settings 320818 A ...
Page 722: ...722 Chapter 13 Viewing system information and performance statistics 320818 A ...
Page 756: ...756 Chapter 14 Maintaining and managing the system 320818 A ...
Page 768: ...768 Chapter 15 Upgrading or reinstalling the software 320818 A ...
Page 802: ...802 Chapter 17 Configuration example 320818 A ...
Page 880: ...880 Appendix C Supported MIBs 320818 A ...
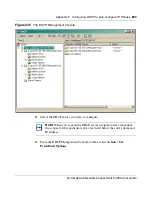
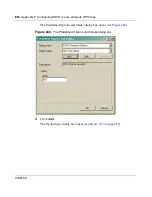
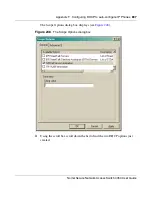
Page 900: ...900 Appendix F Configuring DHCP to auto configure IP Phones 320818 A ...