6 Security User Guide / Security Advisories
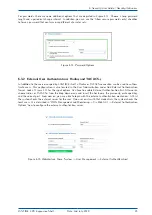
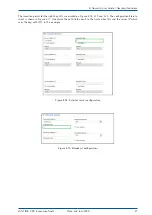
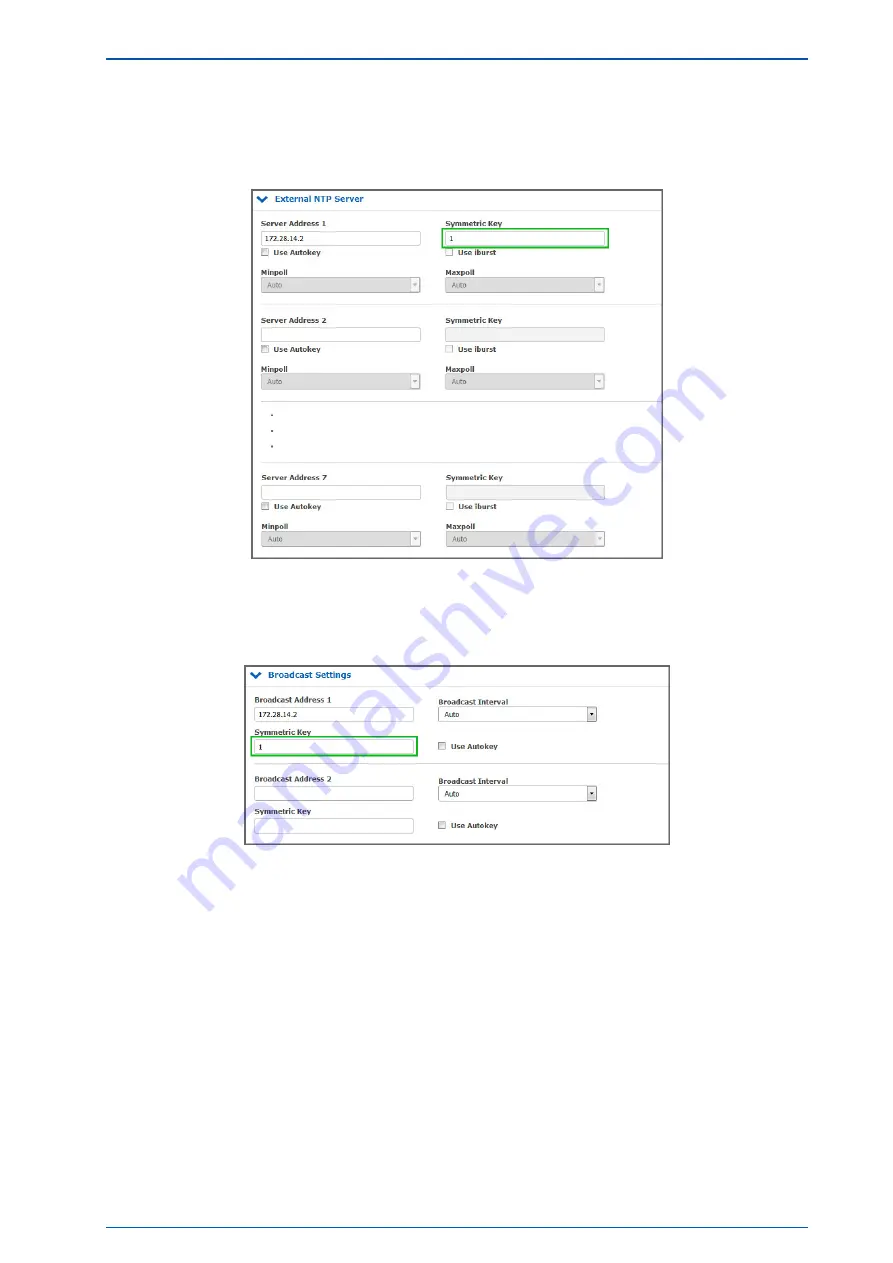
The insertion points for the right key IDs are marked on Figure
and
. The configuration file of a
client is shown in Figure
. It contains the path to the key file, the trusted key IDs and the server IP which
uses the key with ID 1 in this example.
Figure 6.18: External server configuration
Figure 6.19: Broadcast configuration
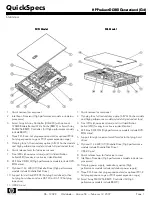
LANTIME CPU Expansion Shelf
Date: 2nd July 2020
27