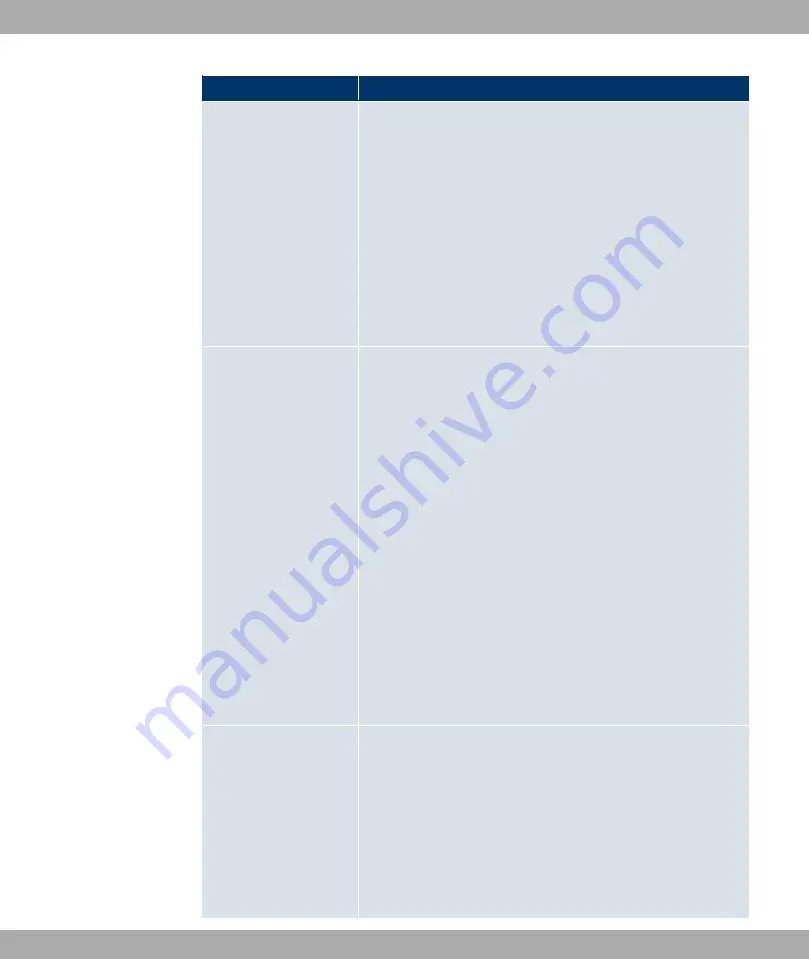
Field
Description
Hash algorithms (Authentication):
•
MD 5
(default value): MD 5 (Message Digest #5) is an older
hash algorithm. It is used with a 96 bit digest length for IPSec.
•
-ALL-
: All options can be used.
•
SHA 1
: SHA1 (Secure Hash Algorithm #1) is a hash al-
gorithm developed by the NSA (United States National Secur-
ity Association). It is rated as secure, but is slower than MD5.
It is used with a 96 bit digest length for IPSec.
Note that RipeMD 160 and Tiger 192 are not available for mes-
sage hashing in phase 2.
Use PFS Group
As PFS (Perfect Forward Secrecy) requires another Diffie-
Hellman key calculation to create new encryption material, you
must select the exponentiation features. If you enable PFS ( En-
abled), the options are the same as for the configuration in
Phase 1: Group. PFS is used to protect the keys of a renewed
phase 2 SA, even if the keys of the phase 1 SA have become
known.
The field has the following options:
•
1 (768-bit)
: During the Diffie-Hellman key calculation,
modular exponentiation at 768 bits is used to create the en-
cryption material.
•
2 (1024 Bit)
(default value): During the Diffie-Hellman key
calculation, modular exponentiation at 1024 bits is used to
create the encryption material.
•
5 (1536-bit)
: During the Diffie-Hellman key calculation,
modular exponentiation at 1536 bits is used to create the en-
cryption material.
Lifetime
Define how the lifetime is defined that will expire before phase 2
SAs need to be renewed.
The new SAs are negotiated shortly before expiry of the current
SAs. As for RFC 2407, the default value is eight hours, which
means the key must be renewed once eight hours have
elapsed.
The following options are available for defining the lifetime:
11 VPN
Funkwerk Enterprise Communications GmbH
332
bintec R1xxx/R3xxx/R4xxx
















































