Using the Command-Line Interface
Check Point IP690 Security Platform Installation Guide
39
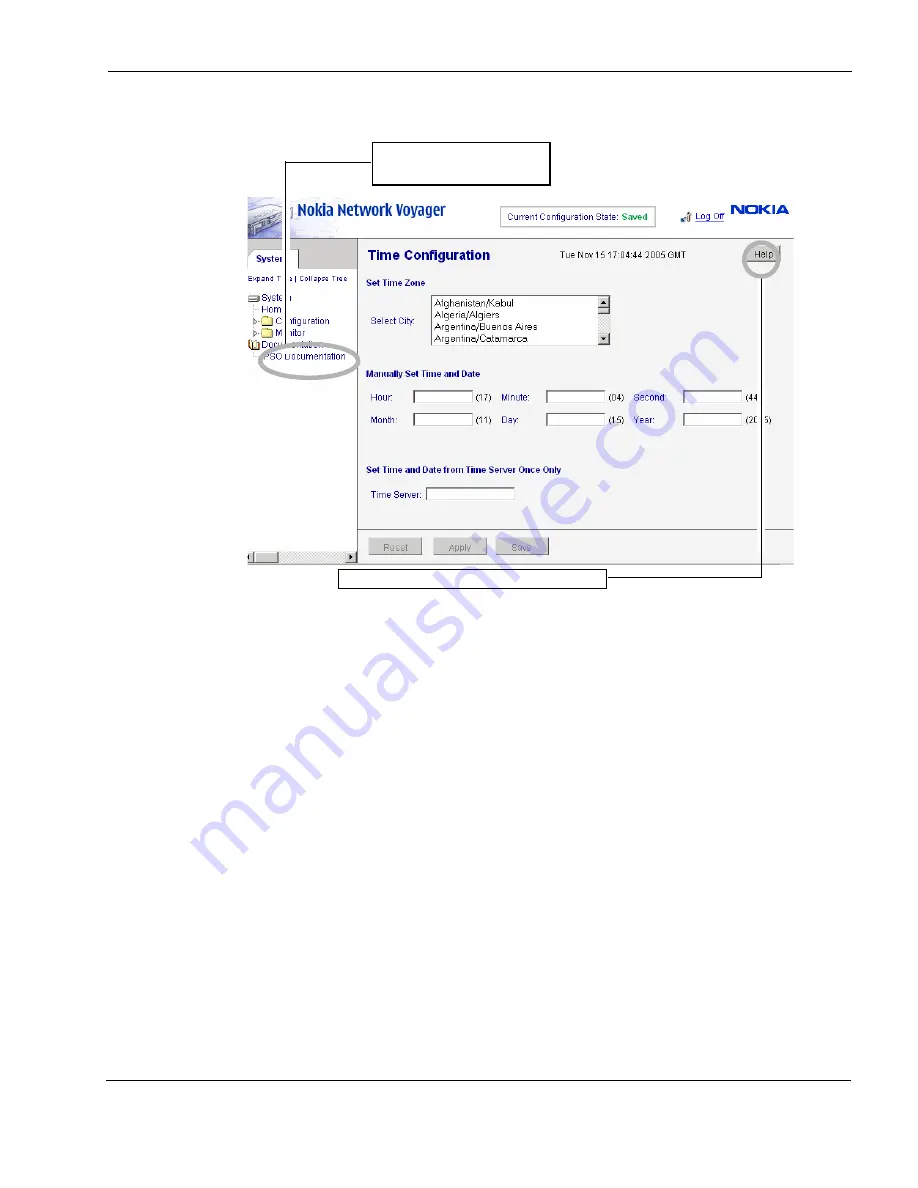
Figure 10 Check Point Network Voyager Reference Access Points
Using the Command-Line Interface
You can also use the Check Point IPSO command-line interface (CLI) to manage and configure
Check Point IP security appliances from the command line. Nearly everything that you can
accomplish with Check Point Network Voyager you can also do with the CLI.
To access the command-line interface
1.
Log on to the appliance by using a command-line connection (SSH, console, or Telnet) over
a TCP/IP network as an admin, cadmin, or monitor user:
If you log in as a cadmin (cluster administrator) user, you can change and view
configuration settings on all the cluster nodes. For information about how to administer a
cluster, see the traffic management commands section in the
CLI Reference Guide
for the
version of Check Point IPSO you are using.
2.
If you log in as a monitor user, you can execute only the show form of commands. That is,
you can view configuration settings, but you cannot change them.
You can now execute CLI commands from the CLI shell and the Check Point IPSO shell. The
Check Point IPSO shell is what you see when you initially log on to the appliance.
Link to complete user
documentation
Link to online help (context sensitive help)
Summary of Contents for IP690 - Flash Based Sys
Page 6: ...6 Check Point IP690 Security Platform Installation Guide...
Page 8: ...8 Check Point IP690 Security Platform Installation Guide...
Page 10: ...10 Check Point IP690 Security Platform Installation Guide...
Page 26: ...1 Overview 26 Check Point IP690 Security Platform Installation Guide...
Page 110: ...A Technical Specifications 110 Check Point IP690 Security Platform Installation Guide...
Page 118: ...Index 118 Check Point IP690 Security Platform Installation Guide...






























