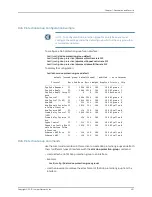
Configurable Options
You can configure the following options for suspicious flow detection:
•
Global on or off. When the option is set to off, flows or packets are not marked as
suspicious. The default is on.
•
Actions a line module takes when the suspicious flow table on the line module
overflows:
•
Overflow—Stop recognizing new suspicious flows
•
Group—Group flows into logical groupings where some individual flows are monitored
as a group
•
Suspicious threshold for each protocol. The threshold is the rate in packets per second
at which a flow becomes suspicious. A zero setting disables suspicious flow detection
for the protocol. Flows are subject to protocol and priority rate limits, but not to
suspicious flow detection.
•
Low threshold for each protocol. The threshold rate determines whether an interface
transitions from suspicious back to nonsuspicious. A zero setting means that the flow
does not transition back to nonsuspicious based on packet rate.
•
Backoff time in seconds for each protocol. After this period expires, the flow transitions
to nonsuspicious regardless of the current rate. When set to zero, an interface does
not return to the nonsuspicious state using a time mechanism.
You can also clear the following:
•
All suspicious flows from the suspicious flow table for a specific slot.
•
Suspicious flows from the suspicious flow table for the entire system.
•
A single suspicious flow; returns the flow to the nonsuspicious state.
Display Options
For monitoring purposes, you can:
•
Display all suspicious control flows when the system has recognized an attack.
•
Display the current state and the number of transitions into suspicious state for the
protocol and priority.
•
Display historical counts about the number of flows made suspicious.
•
View a trap or log generated when a control flow is considered suspicious.
•
View a trap or log generated when a control flow is no longer suspicious.
Traps and Logs
The system generates a trap and a log message under the following conditions:
Copyright © 2010, Juniper Networks, Inc.
438
JunosE 11.3.x System Basics Configuration Guide
Содержание JUNOSE 11.3
Страница 6: ...Copyright 2010 Juniper Networks Inc vi...
Страница 8: ...Copyright 2010 Juniper Networks Inc viii JunosE 11 3 x System Basics Configuration Guide...
Страница 24: ...Copyright 2010 Juniper Networks Inc xxiv JunosE 11 3 x System Basics Configuration Guide...
Страница 32: ...Copyright 2010 Juniper Networks Inc 2 JunosE 11 3 x System Basics Configuration Guide...
Страница 146: ...Copyright 2010 Juniper Networks Inc 116 JunosE 11 3 x System Basics Configuration Guide...
Страница 166: ...Copyright 2010 Juniper Networks Inc 136 JunosE 11 3 x System Basics Configuration Guide...
Страница 432: ...Copyright 2010 Juniper Networks Inc 402 JunosE 11 3 x System Basics Configuration Guide...
Страница 488: ...Copyright 2010 Juniper Networks Inc 458 JunosE 11 3 x System Basics Configuration Guide...
Страница 524: ...Copyright 2010 Juniper Networks Inc 494 JunosE 11 3 x System Basics Configuration Guide...
Страница 554: ...Copyright 2010 Juniper Networks Inc 524 JunosE 11 3 x System Basics Configuration Guide...
Страница 566: ...Copyright 2010 Juniper Networks Inc 536 JunosE 11 3 x System Basics Configuration Guide...
Страница 588: ...Copyright 2010 Juniper Networks Inc 558 JunosE 11 3 x System Basics Configuration Guide...
Страница 613: ...PART 3 Index Index on page 585 583 Copyright 2010 Juniper Networks Inc...
Страница 614: ...Copyright 2010 Juniper Networks Inc 584 JunosE 11 3 x System Basics Configuration Guide...
Страница 632: ...Copyright 2010 Juniper Networks Inc 602 JunosE 11 3 x System Basics Configuration Guide...