6: Networking
EMG™ Edge Management Gateway User Guide
91
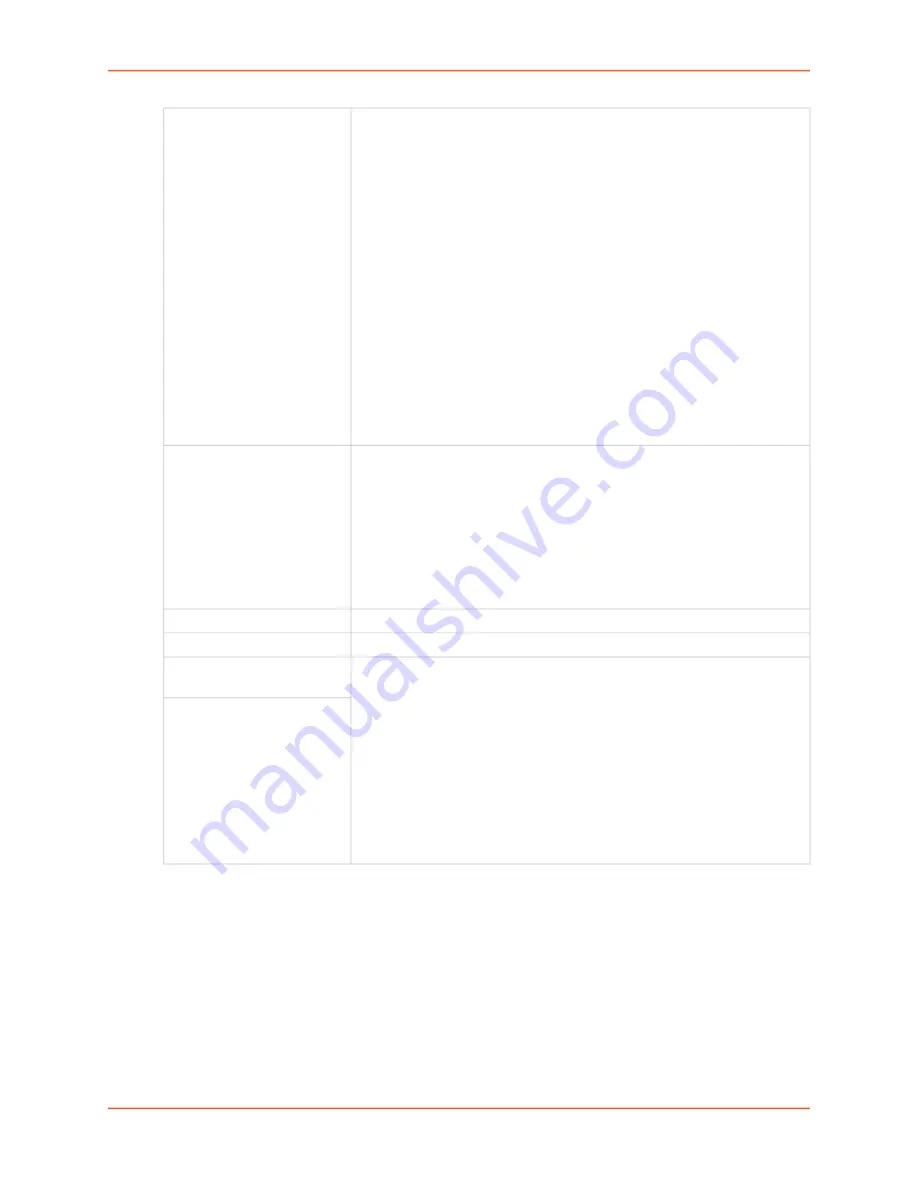
Authentication
The type of authentication used by the host on each side of the VPN tunnel
to verify the identity of the other host.
For
RSA Public Key
, each host generates a RSA public-private key pair,
and shares its public key with the remote host. The RSA Public Key for
the EMG (which has 4096 bits) can be viewed at either the web or CLI.
For
Pre-Shared Key
, each host enters the same passphrase to be used
for authentication.
For
X.509 Certificate
, each host is configured with a Certificate Authority
certificate along with a X.509 certificate with a corresponding private key,
and shares the X.509 certificate with the remote host.
Before using RSA Public Key authentication, select
Generate EMG RSA
Key
to generate the EMG’s RSA public/private key pair. This RSA key can
be regenerated at any time.
Note:
strongSwan does not support IKEv1 aggressive mode with Pre-
Shared Key authorization without XAUTH enabled. If a tunnel is initiated
with this configuration the log message
Aggressive Mode PSK
disabled for security reasons
will be displayed, and a tunnel
will not be initiated. It is possible to override this behavior, but it is not
recommended.
RSA Public Key for
Remote Peer
If
RSA Public Key
is selected for authentication, the remote peer's public
key can be uploaded or deleted. If a public key has been uploaded this field
will display key installed. The peer RSA public key must be in Privacy
Enhanced Mail (PEM) format, e.g.:
-----BEGIN PUBLIC KEY-----
(certificate in base64 encoding)
-----END PUBLIC KEY-----
Pre-Shared Key
If
Pre-Shared Key
is selected for authentication, enter the key.
Retype Pre-Shared Key
If
Pre-Shared Key
is selected for authentication, re-enter the key.
Certificate Authority for
Remote Peer
A certificate can be uploaded to the EMG unit for peer authentication. The
certificate for the remote peer is used to authenticate the EMG to the remote
peer, and at a minimum contains the public certificate file of the remote
peer. The certificate may also contain a Certificate Authority file; if the
Certificate Authority file is omitted, the EMG may display "issuer cacert not
found" and "X.509 certificate rejected" messages, but still authenticate. The
Certificate Authority file and public certificate File must be in PEM format,
e.g.:
-----BEGIN CERTIFICATE-----
(certificate in base64 encoding)
-----END CERTIFICATE-----
Certificate File for Remote
Peer