6: Networking
EMG™ Edge Management Gateway User Guide
89
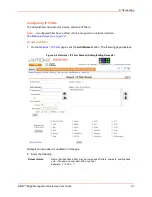
IKE Negotiation
The Internet Key Exchange (IKE) protocol is used to exchange security
options between two hosts who want to communicate via IPSec. The first
phase of the protocol authenticates the two hosts to each other and
establishes the Internet Security Association Key Management Protocol
Security Association (ISAKMP SA). The second phase of the protocol
establishes the cryptographic parameters for protecting the data passed
through the tunnel, which is the IPSec Security Association (IPSec SA). The
IPSec SA can periodically be renegotiated to ensure security.
The IKE protocol can use one of two modes:
Main Mode
, which provides
identity protection and takes longer, or
Aggressive Mode
, which provides
no identity protection but is quicker. With Aggressive Mode, there is no
negotiation of which cryptographic parameters will be used; each side must
give the correct cryptographic parameters in the initial package of the
exchange, otherwise the exchange will fail. If Aggressive Mode is used, the
IKE Encryption
,
IKE Authentication
, and
IKE DH Group
must be
specified.
IKE Version
IKE Version settings to be used. Currently the accepted values are IKEv1,
IKEv2 and Any. Default is IKEv2. Any uses IKEv2 when initiating but will
accept any protocol version while responding.
It is recommended that any IKE Encryption or ESP Encryption parameters
that are selected be supported by the IKE Version that is used. Refer to the
list of
cipher suites for more information.
IKE Encryption
The type of encryption,
3DES
,
AES
,
AES192
or
AES256
, used for IKE
negotiation. Any can be selected if the two sides can negotiate which type of
encryption to use.
Note:
If IKE Encryption, Authentication and DH Group are set to
Any
,
default cipher suite(s) will be used. If the console manager acts as an
initiator, the tunnel will use a default IKE cipher of aes128-sha256-ecp256
(for IKEv1). For IKEv2 or when the console manager is the responder in
tunnel initiation, it will propose a set of cipher suites and will accept the first
supported proposal received from the peer.
IKE Authentication
The type of authentication,
SHA2_256
,
SHA2_384
,
SHA2_512
,
SHA1,
or
MD5
, used for IKE negotiation.
Any
can be selected if the two sides can
negotiate which type of authentication to use.
IKE DH Group
The Diffie-Hellman Group, 2 (modp1024), 5 (modp1536), 14 (modp2048),
15 (modp3072), 16 (modp4096), 17 (modp6144), 18 (modp8192) or 19
(ecp256) can be used for IKE negotiation. Any can be selected if the two
sides can negotiate which Diffie-Hellman Group to use.