Proactive Defense
121
The types of activity that Proactive Defense monitors are listed in the
Settings:
Application Activity Analyzer
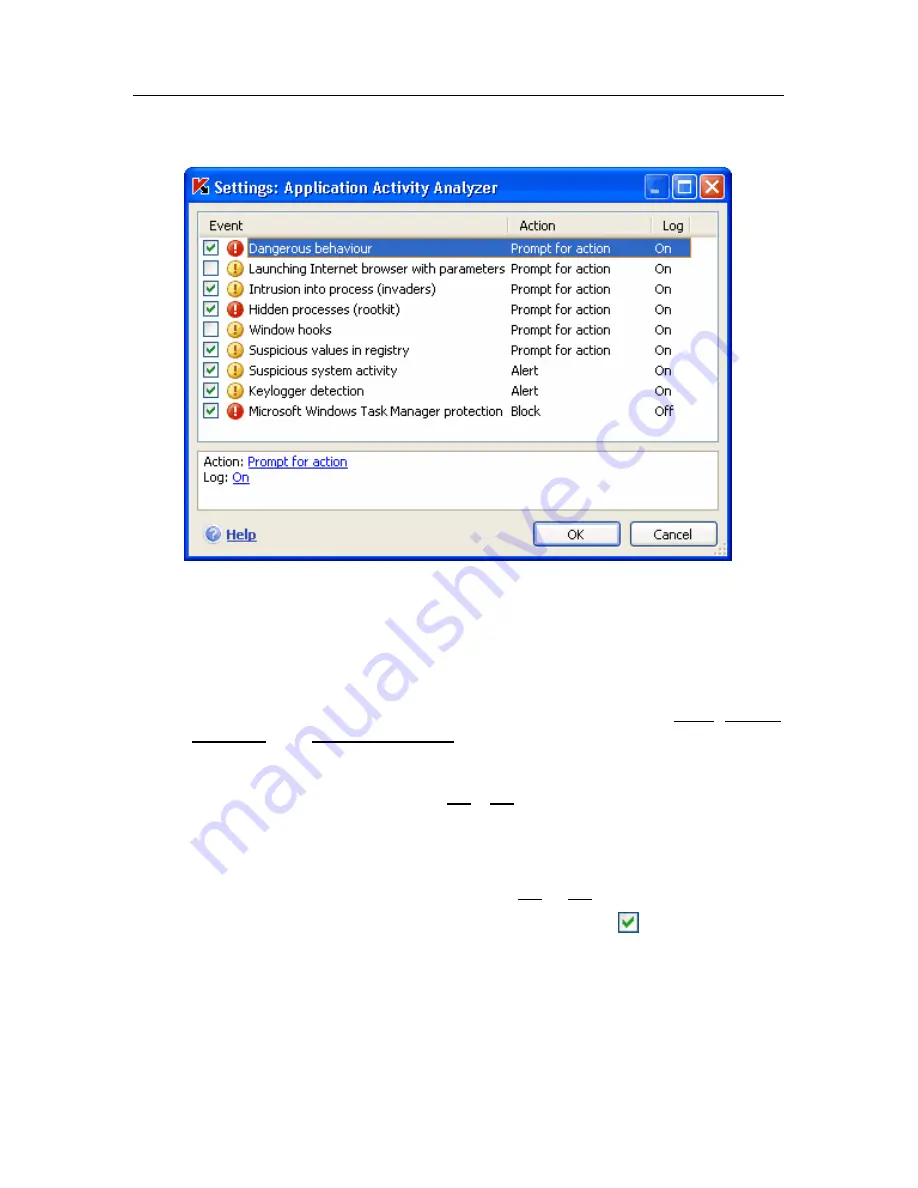
window (see fig. 33).
Figure 33. Configuring application activity control
To edit a dangerous activity monitoring rule, select it from the list and assign the
rule settings in the lower part of the tab:
•
Assign the Proactive Defense response to the dangerous activity.
You can assign any of the following actions as a response: allow, prompt
for action, and terminate process. Left-click on the link with the action until
it reaches the value that you need. In addition to stopping the process,
you can place the application that initiated the dangerous activity in
Quarantine. To do so, use the On / Off link across from the appropriate
setting. You can assign a time value for how frequently the scan will run
for detecting hidden processes in the system.
•
Choose if you want to generate a report on the operation carried out. To
do so, click on the
Log
link until it shows On or Off as required .
To turn off monitoring for a dangerous activity, uncheck the next to the name
in the list. Proactive Defense will no longer analyze that type of activity.
Specifics of configuring application activity control in Kaspersky Internet
Security under Microsoft Windows XP Professional x64 Edition, Microsoft
Windows Vista, or Microsoft Windows Vista x64:






























