51
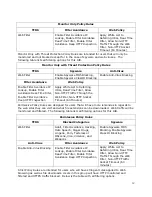
Strict Policy Rules
TFRS
Blocked Categories
Blocked File Types
Web Anonymous
Proxy Guard + SSL Block
Adult, Alcohol and Tobacco, Cars
and Motorcycles, Cheating and
Plagiarism, Crime, Criminal
Related, Cults, Dating, Filter
Avoidance, FYI, Gambling,
Games, Hacking, Hate Speech,
Illegal Drugs, Instant Messaging,
Job Search, Lingerie, Lottery and
Sweepstakes, Non-mainstream,
Non-sexual Nudity, Online
Communities, Online Trading,
Peer File Transfer, Porn, Real
Estate, Sex Ed and Abortion,
Shopping, Sports and
Recreation, Streaming Media,
Tasteless or Obscene, Tattoos,
Vice, Violence, Weapons, Web
Messaging, Web-based Chat,
Web-based Email
aac, adp, aiff, asx, avi,
bat, cab, cmd, com, dll,
dmg, ed2k, emo, exe, flac,
flv, fpt, ini, iso, kmz, lit,
lnk, log, m3u, m4a, mid,
midi, moov, mov, mp3,
mp4, mpeg, mpg, mpu,
msi, mst, ogg, ogm, pab,
pls, qt, ra, ram, rm,
torrent, wav, wma, wmf,
wmv
Spyware
Anti-Virus
Filter Avoidance
Enable Spyware URL
Blocking, Enable Spyware
MD5 Blocking, Enable
Spyware ClassID Blocking
Enable Anti-Virus Blocking
Enable Filter Avoidance IP
Lookup, Enable Filter
Avoidance Real-Time Filter,
Enable Filter Avoidance
Deep HTTP Inspection
Web Policy
Enable Safe Search
Protection for Search
Engines, Block Search
Engine Cached Pages,
Real-Time Filter, Enable
Reverse DNS Lookups,
Block IP Address URLs
Again, these are the default IURs available for ease of use. You may simply add users to
these groups for the policy to apply. You can also alter all default IURs except for Deny
Access Usage Rules and Filter Bypass Usage Rules by selecting the individual IURs under
Internet Usage Rule Manager. If you would like to create you own IUR, select the Create
button under Internet Usage Rule Manager.
Shaping Rules
Shaping Rules allow you to “shape” network bandwidth for applications, users, and web
sites. In essence, Shaping Rules allow you to cap or restrict bandwidth for specific users or
applications on the network. These rules also allow you to shape bandwidth to Web sites as
well as assign priority levels for all traffic. Through Shaping Rules, you can control and
manage network traffic to ensure that critical users and applications have complete access
to the Internet and network resources.