61
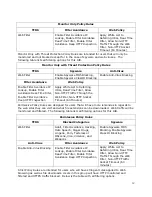
There are several default TFRS that can do some of these options; however, there is no one
TRFS that has all components (Web Deny IM + SSL Block). Nevertheless, the
Traffic Flow Rule Set Manager allows you to combine or delete components of the TFRS to
tailor how traffic will be handled.
Select Manage -> Applications -> Traffic Flow Rule Sets. Rather than editing the default
TFRS, you can copy them and make the necessary changes to create a custom TFRS.
Although you can select the default TFRS and edit them, it is highly recommended that
you do not edit default TFRS. Doing so can cause severe problems if the TFRS are
configured incorrectly. You are better served by copying default TFRS and editing the
copies.
The key factor in creating a custom TFRS is to choose a default one that closely represents
the end result. For this example, we will select to copy the TFRS of Web Deny IM
and afterwards add the component of SSL Block. Copying TFRS is quite simple: select the
checkbox next to the TFRS that is going to be copied and select the Copy Selected button.
This will bring up the Add/Edit Traffic Flow Rule Set field. Here, you can create a distinct
name and description for the custom TFRS. This field also allows you to remove certain
applications for the TFRS. For example, if you didn’t want this TFRS to identify ICMP traffic,
you could remove this application using the < Remove button. More often than not, you will
only want to customize the name and description in this field as removing applications can
cause unexpected effects. Another suggestion is to name the TFRS according to the
targets. In our example, we would name the TFRS Web Deny IM + SSL Block.
Again, don’t forget to Save your changes.
Once you have created a custom TFRS, you will alter the targets according to the desired
modifications. This is done under the Application Signature Manager (covered later under
the Applications section). In our example, we will need to alter the SSL targets to block this
traffic. Now that we have created a custom TFRS to block SSL traffic, we will need to alter
the targets. The steps to alter targets are covered under the next sections.
Other options available under the Traffic Flow Rule Set Manager are deleting and creating.
There is also a search box to search available TFRS. Now let’s continue our example of a
custom TFRS by discussing the Application Sets and Applications menus. The following
sections will give a brief explanation of the options available and a common example of
configuration changes.
Application Sets
Application sets, or simply signature sets, are groups of signatures for similar applications
that perform a comparable purpose. For example, the signature set of Remote Desktop
/Remote Control /X comprises the applications of PC Anywhere, Citrix, GoToMyPC,
Microsoft’s Remote Desktop, and many more. Because these applications use similar
signatures and perform an equivalent purpose (connecting users remotely to computers)
the different applications are grouped together in an Application set.
The Application Signature Set Manager (Manage -> Applications -> Application Sets) lists all
sets of applications that Optinet can identify and shape. Currently there are 23 Application
Sets that Optinet identifies.