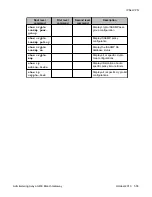
Root level
command
First level
command
Second level
command
Description
ip crypto-
group
Activate a crypto list in the
context of the interface on
which the crypto list is activated
ip crypto-list
Enter crypto list context and
create or edit a crypto list
ip-rule
Enter ip-rule context and create
or modify a specific rule
descriptio
n
Enter a description for the ip-
rule in the ip crypto list
destinatio
n-ip
Specify the destination IP
address of packets to which the
current rule applies
protect
crypto map
Protect traffic that matches this
rule by applying the IPSec
processing configured by the
specific crypto map
source-ip
Indicate that the current rule
applies to packets from the
specified source IP address
local-
address
Set the local IP address for the
IPSec tunnels derived from this
crypto list
show crypto
ipsec sa
Display the IPSec SA database
and related runtime, statistical,
and configuration information
Note:
The
detail
option in the
various
show crypto
ipsec sa
commands,
provides detailed counters
information on each IPSec
SA. To pinpoint the source of
a problem, it is useful to
check for a counter whose
value grows with time.
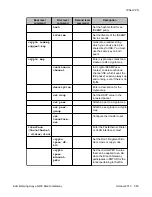
show crypto
ipsec
transform-set
Display the configuration for the
specified transform-set or all
transform-sets
show crypto
isakmp peer
Display crypto ISAKMP peer
configuration
IPSec VPN
554 Administering Avaya G430 Branch Gateway
October 2013
Summary of Contents for G430
Page 1: ...Administering Avaya G430 Branch Gateway Release 6 3 03 603228 Issue 5 October 2013 ...
Page 12: ...12 Administering Avaya G430 Branch Gateway October 2013 ...
Page 246: ...VoIP QoS 246 Administering Avaya G430 Branch Gateway October 2013 Comments infodev avaya com ...
Page 556: ...IPSec VPN 556 Administering Avaya G430 Branch Gateway October 2013 Comments infodev avaya com ...