Procedure
1. Use the
show rtp-stat sessions
command to display a summary of the active
and/or terminated RTP sessions in the session table.
For example:
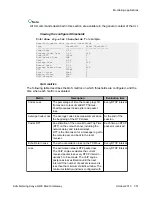
Gxxx-001(super)# show rtp-stat sessions last 5
ID QoS Start date and time End Time Type Destination
----- --- ------------------- -------- ------- ---------------
00031 2004-10-20,10:51:36 10:59:07 G729 135.8.76.64
00032 * 2004-10-20,10:53:42 10:57:36 G723 135.8.76.107
00033 * 2004-10-20,10:58:21 10:59:06 G723 135.8.76.107
00034 2004-10-20,11:08:40 - G729 135.8.76.64
00035 * 2004-10-20,11:09:07 - G723 135.8.76.107
An asterisk (*) in the QoS column indicates that the session had QoS problems.
2. Use the
show rtp-stat detailed
command to display detailed information
about a specified active or terminated RTP session, including the QoS metrics
reported by the RTP statistics application.
For example:
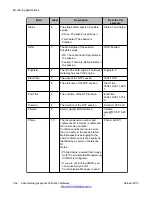
Gxxx-001(super)# show rtp-stat detailed 35
Session-ID: 35
1
Status: Terminated
2
, QOS: Faulted
3
, EngineId: 0
4
Start-Time: 2004-10-20
5
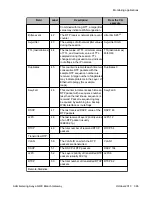
,11:09:07
6
, End-Time: 2004-10-20,11:13:40
7
Duration: 00:04:33
8
CName: [email protected]
9
Phone: 69:2011
10
Local-Address: 135.8.118.252:2061
11
SSRC 154611212
12
Remote-Address: 135.8.76.107:2061
13
SSRC 2989801899 (0)
14
Samples: 54
15
(5 sec)
16
Codec:
G723
17
62B
18
30mS
19
Off
20
, Silence-suppression(Tx/Rx) Disabled
21
/Not-Supported
22
,
Play-Time 272.610sec
23
, Loss 0.0%
24
#1
25
, Avg-Loss 0.1%
26
, RTT 741mS
27
#38
28
,
Avg-RTT 570mS
29
, JBuf-under/overruns 0.1%
30
/0.0%
31
, Jbuf-Delay 22mS
32
Monitoring applications
360 Administering Avaya G430 Branch Gateway
October 2013
Summary of Contents for G430
Page 1: ...Administering Avaya G430 Branch Gateway Release 6 3 03 603228 Issue 5 October 2013 ...
Page 12: ...12 Administering Avaya G430 Branch Gateway October 2013 ...
Page 246: ...VoIP QoS 246 Administering Avaya G430 Branch Gateway October 2013 Comments infodev avaya com ...
Page 556: ...IPSec VPN 556 Administering Avaya G430 Branch Gateway October 2013 Comments infodev avaya com ...