ProSecure Web/Email Security Threat Management (STM) Appliance Reference Manual
6-12
Monitoring System Access and Performance
v1.0, September 2009
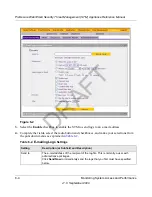
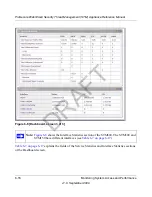
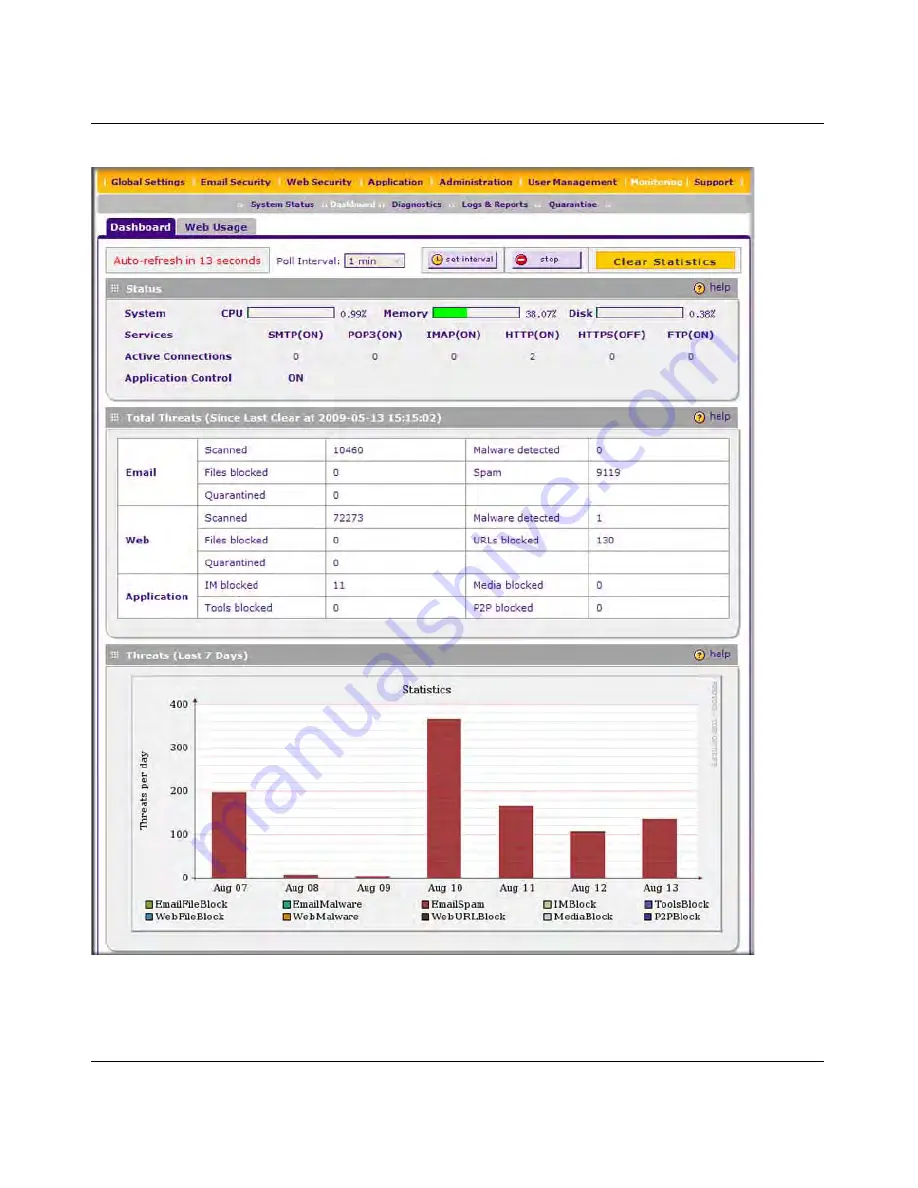
Table 6-5 on page 6-13
explains the fields of the Status, Total Threats, Threats (Last 7 Days)
sections of the Dashboard screen.
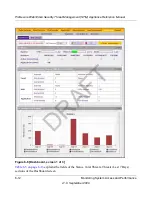
Figure 6-6 [Dashboard, screen 1 of 3]
DRAFT
Содержание STM150 - ProSecure Web And Email Threat Management Appliance
Страница 6: ...v1 0 September 2009 vi D R A F T ...