5 - 144 WiNG 5.6 Access Point System Reference Guide
5.2.7.2 Auto IPSec Tunnel
Profile Security Configuration
IPSec tunnels are established to secure traffic, data and management traffic, from access points to remote wireless controllers.
Secure tunnels must be established between access points and the wireless controller with minimum configuration pushed
through DHCP option settings.
1. Select the
Configuration
tab from the Web UI.
2. Select
Devices
.
3. Select
System Profile
from the options on left-hand side of the UI.
4. Expand the
Security
menu and select
Auto IPSec Tunnel
.
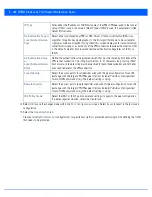
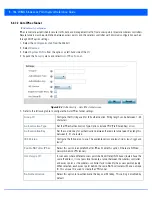
Figure 5-92
Profile Security – Auto IPSec Tunnel screen
5. Refer to the following table to configure the Auto IPSec Tunnel settings:
Group ID
Configure the ID string used for IKE authentication. String length can be between 1 - 64
characters.
Authentication Type
Set the IPSec Authentication Type. Options include
PSK
(Pre Shared Key) or
rsa.
Authentication Key
Set the common key for authentication between the remote tunnel peer. Key length is
between 8 - 21 characters.
IKE Version
Configure the IKE version to use. The available options are
ikev1-main
,
ikev1-aggr
and
ikev2.
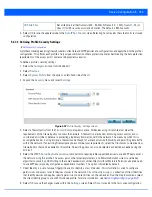
Enable NAT after IPSec
Select this option to enable NAT after IPSec. Enable this option if there are NATted
networks behind VPN tunnels.
Use Unique ID
In scenarios where different access points behind different NAT boxes/routers have the
same IP address, it is not possible to create a tunnel between the wireless controller
and access point, as the wireless controller fails to identify the access point uniquely.
When selected, each access point behind the same NAT box/router will have a unique
ID. This unique ID is used to create the VPN tunnel.
Re-Authentication
Select this option to re-authenticate the key on a IKE rekey. This setting is disabled by
default.
Содержание WiNG 5.6
Страница 1: ...Motorola Solutions WiNG 5 6 ACCESS POINT SYSTEM REFERENCE GUIDE ...
Страница 2: ......
Страница 3: ...MOTOROLA SOLUTIONS WING 5 6 ACCESS POINT SYSTEM REFERENCE GUIDE MN000335A01 Revision A March 2014 ...
Страница 22: ...8 WiNG 5 6 Access Point System Reference Guide ...
Страница 26: ...1 4 WiNG 5 6 Access Point System Reference Guide ...
Страница 38: ...2 12 WiNG 5 6 Access Point System Reference Guide ...
Страница 74: ...3 36 WiNG 5 6 Access Point System Reference Guide ...
Страница 468: ...6 2 WiNG 5 6 Access Point System Reference Guide Figure 6 1 Configuration Wireless menu ...
Страница 568: ...6 102 WiNG 5 6 Access Point System Reference Guide ...
Страница 614: ...7 46 WiNG 5 6 Access Point System Reference Guide ...
Страница 660: ...8 46 WiNG 5 6 Access Point System Reference Guide ...
Страница 664: ...9 4 WiNG 5 6 Access Point System Reference Guide Figure 9 2 Captive Portal Policy screen Basic Configuration tab ...
Страница 716: ...9 56 WiNG 5 6 Access Point System Reference Guide ...
Страница 730: ...10 14 WiNG 5 6 Access Point System Reference Guide ...
Страница 776: ...12 36 WiNG 5 6 Access Point System Reference Guide Figure 12 46 Device Summary screen 4 Click File Management ...
Страница 792: ...12 52 WiNG 5 6 Access Point System Reference Guide Figure 12 60 Certificate Management Import New Trustpoint screen ...
Страница 982: ...14 20 WiNG 5 6 Access Point System Reference Guide ...
Страница 984: ...A 2 WiNG 5 6 Access Point System Reference Guide ...
Страница 1046: ...B 62 WiNG 5 6 Access Point System Reference Guide ...
Страница 1047: ......