8 - 16 WiNG 5.6 Access Point System Reference Guide
8.2 Configuring IP Firewall Rules
Security Configuration
Access points use IP based firewalls like
Access Control Lists
(ACLs) to filter/mark packets based on the IP address from which
they arrive, as opposed to filtering packets on Layer 2 ports.
IP based firewall rules are specific to source and destination IP addresses and the unique rules and precedence orders
assigned. Both IP and non-IP traffic on the same Layer 2 interface can be filtered by applying an IP ACL. Firewall rules are
processed by a firewall supported device from first to last. When a rule matches the network traffic an access point is
processing, the firewall uses that rule's action to determine whether traffic is allowed or denied.
There are separate policy creation mechanisms for IPv4 and IPv6 traffic. With either IPv4 or IPv6, create access rules for traffic
entering an access point interface, because if you are going to deny specific types of packets, it is recommended you do it
before the access point spends time processing them, since access rules are processed before other types of firewall rules.
IPv6 addresses are composed of eight groups of four hexadecimal digits separated by colons.
For more information, see:
•
Setting an IPv4 or IPv6 Firewall Policy
•
Setting an IP SNMP ACL Policy
8.2.1 Setting an IPv4 or IPv6 Firewall Policy
Configuring IP Firewall Rules
Before defining a firewall configuration, refer to the following deployment guidelines to ensure the configuration is optimally
effective:
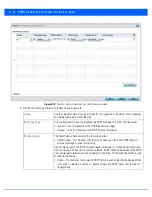
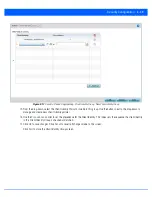
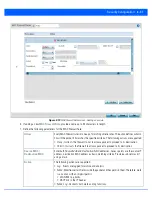
To add or edit an IP based Firewall Rule policy:
1. Select
Configuration
tab from the Web user interface.
2. Select
Security
.
3. Select
IPv4 ACL
or
IPv6 ACL
to display existing IP firewall policies.
NOTE:
Once defined, a set of IP firewall rules must be applied to an interface to be a
functional filtering tool.
Содержание WiNG 5.6
Страница 1: ...Motorola Solutions WiNG 5 6 ACCESS POINT SYSTEM REFERENCE GUIDE ...
Страница 2: ......
Страница 3: ...MOTOROLA SOLUTIONS WING 5 6 ACCESS POINT SYSTEM REFERENCE GUIDE MN000335A01 Revision A March 2014 ...
Страница 22: ...8 WiNG 5 6 Access Point System Reference Guide ...
Страница 26: ...1 4 WiNG 5 6 Access Point System Reference Guide ...
Страница 38: ...2 12 WiNG 5 6 Access Point System Reference Guide ...
Страница 74: ...3 36 WiNG 5 6 Access Point System Reference Guide ...
Страница 468: ...6 2 WiNG 5 6 Access Point System Reference Guide Figure 6 1 Configuration Wireless menu ...
Страница 568: ...6 102 WiNG 5 6 Access Point System Reference Guide ...
Страница 614: ...7 46 WiNG 5 6 Access Point System Reference Guide ...
Страница 660: ...8 46 WiNG 5 6 Access Point System Reference Guide ...
Страница 664: ...9 4 WiNG 5 6 Access Point System Reference Guide Figure 9 2 Captive Portal Policy screen Basic Configuration tab ...
Страница 716: ...9 56 WiNG 5 6 Access Point System Reference Guide ...
Страница 730: ...10 14 WiNG 5 6 Access Point System Reference Guide ...
Страница 776: ...12 36 WiNG 5 6 Access Point System Reference Guide Figure 12 46 Device Summary screen 4 Click File Management ...
Страница 792: ...12 52 WiNG 5 6 Access Point System Reference Guide Figure 12 60 Certificate Management Import New Trustpoint screen ...
Страница 982: ...14 20 WiNG 5 6 Access Point System Reference Guide ...
Страница 984: ...A 2 WiNG 5 6 Access Point System Reference Guide ...
Страница 1046: ...B 62 WiNG 5 6 Access Point System Reference Guide ...
Страница 1047: ......