13 - 124 WiNG 5.6 Access Point System Reference Guide
13.3.24 VPN
Access Point Statistics
IPSec VPN provides a secure tunnel between two networked peer controllers or service platforms. Administrators can define
which packets are sent within the tunnel, and how they are protected. When a tunnelled peer sees a sensitive packet, it creates
a secure tunnel and sends the packet through the tunnel to its remote peer destination.
Tunnels are sets of
security associations
(SA) between two peers. SAs define the protocols and algorithms applied to sensitive
packets and specify the keying mechanisms used by tunnelled peers. SAs are unidirectional and exist in both the inbound and
outbound direction. SAs are established per the rules and conditions of defined security protocols (AH or ESP).
Crypto maps combine the elements comprising IPSec SAs. Crypto maps also include
transform sets
. A transform set is a
combination of security protocols, algorithms and other settings applied to IPSec protected traffic. One crypto map is utilized
for each IPsec peer, however for remote VPN deployments one crypto map is used for all the remote IPsec peers.
Internet Key Exchange
(IKE) protocol is a key management protocol standard used in conjunction with IPSec. IKE enhances
IPSec by providing additional features, flexibility, and configuration simplicity for the IPSec standard. IKE automatically
negotiates IPSec SAs, and enables secure communications without time consuming manual pre-configuration.
VPN statistics are partitioned into the following:
•
IKESA
•
IPSec
13.3.24.1 IKESA
VPN
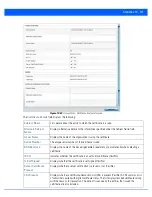
The
IKESA
screen allows for the review of individual peer security association statistics.
1. Select the
Statistics
menu from the Web UI.
2. Select
System
from the navigation pane (on the left-hand side of the screen). Expand a RF Domain and select one of its
connected access points.
3. Select
VPN
and expand the menu to reveal its sub menu items
.
4. Select
IKESA
.
Figure 13-82
Access Point - VPN IKESA screen
Summary of Contents for WiNG 5.6
Page 1: ...Motorola Solutions WiNG 5 6 ACCESS POINT SYSTEM REFERENCE GUIDE ...
Page 2: ......
Page 22: ...8 WiNG 5 6 Access Point System Reference Guide ...
Page 26: ...1 4 WiNG 5 6 Access Point System Reference Guide ...
Page 38: ...2 12 WiNG 5 6 Access Point System Reference Guide ...
Page 74: ...3 36 WiNG 5 6 Access Point System Reference Guide ...
Page 468: ...6 2 WiNG 5 6 Access Point System Reference Guide Figure 6 1 Configuration Wireless menu ...
Page 568: ...6 102 WiNG 5 6 Access Point System Reference Guide ...
Page 614: ...7 46 WiNG 5 6 Access Point System Reference Guide ...
Page 660: ...8 46 WiNG 5 6 Access Point System Reference Guide ...
Page 716: ...9 56 WiNG 5 6 Access Point System Reference Guide ...
Page 730: ...10 14 WiNG 5 6 Access Point System Reference Guide ...
Page 982: ...14 20 WiNG 5 6 Access Point System Reference Guide ...
Page 984: ...A 2 WiNG 5 6 Access Point System Reference Guide ...
Page 1046: ...B 62 WiNG 5 6 Access Point System Reference Guide ...
Page 1047: ......