15-2
Catalyst 3550 Multilayer Switch Software Configuration Guide
78-11194-03
Chapter 15 Configuring SPAN
Understanding SPAN
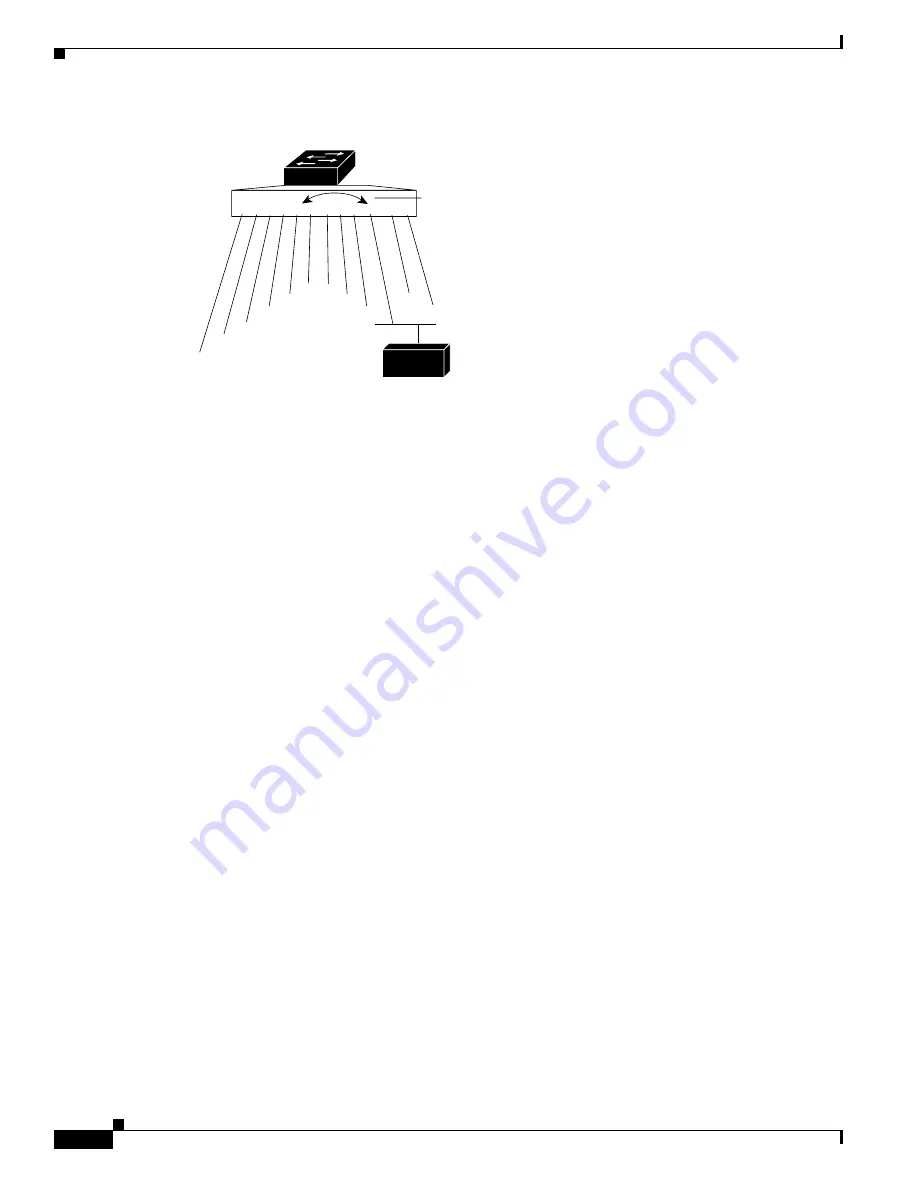
Figure 15-1 Example SPAN Configuration
Only traffic that enters or leaves source ports or traffic that enters source VLANs can be monitored by
using SPAN; traffic that gets routed to ingress source ports or source VLANs cannot be monitored. For
example, if incoming traffic is being monitored, traffic that gets routed from another VLAN to the source
VLAN is not monitored; however, traffic that is received on the source VLAN and routed to another
VLAN is monitored.
This release supports only local SPAN, which means the source and destination interfaces must be on
the same switch.
SPAN does not affect the switching of network traffic on source ports or source VLANs; a copy of the
packets received or sent by the source interfaces are sent to the destination interface. However, an
oversubscribed SPAN destination, for example, a 10-Mbps port monitoring a 100-Mbps port, can cause
congestion on the switch. Destination ports do not receive or forward traffic, except that required for the
SPAN session.
SPAN Concepts and Terminology
This section describes concepts and terminology associated with SPAN configuration.
SPAN Session
A SPAN session is an association of a destination port with source ports or source VLANs. You
configure SPAN sessions by using parameters that specify the type of network traffic to monitor. Traffic
monitoring in a SPAN session has these restrictions:
•
You can monitor incoming traffic on a series or range of ports or VLANs.
•
You can monitor outgoing traffic on a single port; you cannot monitor outgoing traffic on multiple
ports.
•
You cannot monitor outgoing traffic on VLANs.
You can configure two separate SPAN sessions with separate or overlapping sets of SPAN source
VLANs. Both switched and routed ports can be configured as SPAN sources and destinations. SPAN
sessions do not interfere with the normal operation of the switch.
1 2 3 4 5 6 7 8 9 10 11 12
Port 5 traffic mirrored
on Port 10
3
2
1
4
5
6
7
8
9
11
12
10
Network analyzer
43580
















































