Chapter 28 DHCP Snooping
XGS4600 Series User’s Guide
307
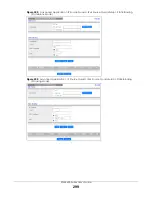
Figure 234
Advanced Application > IP Source Guard > IPv4 Source Guard Setup > DHCP Snooping >
Configure > Port (Stacking Mode)
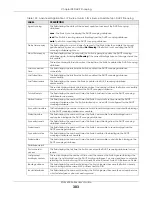
The following table describes the labels in this screen.
Table 127 Advanced Application > IP Source Guard > IPv4 Source Guard Setup > DHCP Snooping >
Configure > Port
LABEL
DESCRIPTION
SLOT
This field appears only in stacking mode. Click the drop-down list to choose the slot number
of the Switch in a stack.
Port
This field displays the port number. In stacking mode, the first number represents the slot ID
and the second is the port number. Please note that the default stacking ports (the last two
ports of your Switch) cannot be configured. They are reserved for stacking only.
*
Settings in this row apply to all ports.
Use this row only if you want to make some settings the same for all ports. Use this row first to
set the common settings and then make adjustments on a port-by-port basis.
Note: Changes in this row are copied to all the ports as soon as you make them.
Server Trusted state
Select whether this port is a trusted port (
Trusted
) or an untrusted port (
Untrusted
).
Trusted ports are connected to DHCP servers or other switches, and the Switch discards
DHCP packets from trusted ports only if the rate at which DHCP packets arrive is too high.
Untrusted ports are connected to subscribers, and the Switch discards DHCP packets from
untrusted ports in the following situations:
• The packet is a DHCP server packet (for example, OFFER, ACK, or NACK).
• The source MAC address and source IP address in the packet do not match any of the
current bindings.
• The packet is a RELEASE or DECLINE packet, and the source MAC address and source
port do not match any of the current bindings.
• The rate at which DHCP packets arrive is too high.
Rate (pps)
Specify the maximum number for DHCP packets (1 – 2048) that the Switch receives from
each port each second. The Switch discards any additional DHCP packets. Enter 0 to
disable this limit, which is recommended for trusted ports.
Apply
Click
Apply
to save your changes to the Switch’s run-time memory. The Switch loses these
changes if it is turned off or loses power, so use the
Save
link on the top navigation panel to
save your changes to the non-volatile memory when you are done configuring.
Cancel
Click this to reset the values in this screen to their last-saved values.
Содержание XGS4600 Series
Страница 24: ...24 PART I User s Guide ...
Страница 44: ...44 PART II Technical Reference ...
Страница 180: ...Chapter 13 Spanning Tree Protocol XGS4600 Series User s Guide 180 Figure 145 MSTP and Legacy RSTP Network Example ...
Страница 189: ...Chapter 16 Mirroring XGS4600 Series User s Guide 189 Figure 150 Advanced Application Mirroring Standalone Mode ...
Страница 244: ...Chapter 22 Policy Rule XGS4600 Series User s Guide 244 Figure 189 Policy Example EXAMPLE ...
Страница 277: ...Chapter 25 Multicast XGS4600 Series User s Guide 277 Figure 215 Advanced Application Multicast MVR Standalone Mode ...
Страница 559: ...Chapter 59 Access Control XGS4600 Series User s Guide 559 Figure 460 Example Lock Denoting a Secure Connection EXAMPLE ...
Страница 586: ...Chapter 69 Configure Clone XGS4600 Series User s Guide 586 Figure 479 Management Configure Clone Standalone Mode ...
Страница 587: ...Chapter 69 Configure Clone XGS4600 Series User s Guide 587 Figure 480 Management Configure Clone Stacking Mode ...
Страница 594: ...Chapter 71 Port Status XGS4600 Series User s Guide 594 Figure 485 Management Port Status Port Details Standalone Mode ...
Страница 604: ...604 PART III Troubleshooting and Appendices ...