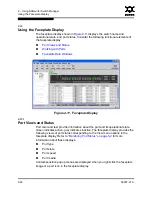
3 – Managing Fabrics
Securing a Fabric
59097-01 A
3-7
0
3.2
Securing a Fabric
Fabric security consists of the following:
Connection Security
User Account Security
Security Consistency Checklist
Device Security
Fabric Services
3.2.1
Connection Security
Connection security provides an encrypted data path for switch management
methods. The switch supports the Secure Shell (SSH) protocol for the command
line interface and the Secure Socket Layer (SSL) protocol for management
applications such as SANsurfer Switch Manager and Common Information
Module (CIM).
The SSL handshake process between the workstation and the switch involves the
exchanging of certificates. These certificates contain the public and private keys
that define the encryption. The switch certificate is valid for one year beginning
with its creation date and time. The workstation validates the switch certificate by
comparing the workstation date and time to the switch certificate creation date and
time. For this reason, it is important to snychronize the workstation and switch with
the same date, time, and time zone. If a certificate has not been created by the
user, the switch will automatically create one.
Consider your requirements for connection security: for the command line
interface (SSH), management applications such as SANsurfer Switch Manager
(SSL), or both. If SSL connection security is required, also consider using the
Network Time Protocol (NTP) to synchronize workstations and switches.