SmartNA-X 1G/10G Modular | SmartNA-X Administration |
35
SmartNA-X
™
1G/10G User Guide 1.4
©
2015 Network Critical Solutions Limited
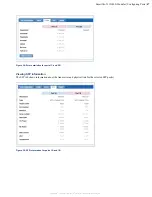
Figure 23: Upload SSL certificate page
3.
Enter the Administrator username and password, and browse to the certificate file.
The certificate file must be in a
.tar.bz2
file format, and must contain the following two files only:
•
NetworkCritical.crt
—X.509 certificate file (PEM-encoded; maximum 8192 bits)
•
server.key
—private key file (PEM-encoded; maximum 8192-bit)
Caution:
Uploading an incorrect certificate could render the device inaccessible to network connections. If
this happens, you should connect via the serial Console port and perform a factory reset with instructions from
Network Critical Support.
4.
Click
Upload new certificate
and wait for the certificate file to be uploaded and verified. All new connections will be
verified using the new public-keys.
Configuring management access
You can assign authentication methods to management access methods, such as SSH, console, and HTTPS. This
authentication can be performed locally or on an external server, such as a or a RADIUS server.
User authentication occurs using the authentication methods that are selected, in no particular order. If the first
authentication method is not available, the next selected method is used. For example, if the selected authentication
methods are RADIUS and Local, and all configured RADIUS servers are queried in priority order and do not reply,
the user is authenticated locally. If an authentication method fails or the user has insufficient privilege level, the user is
denied access to the device. In other words, if authentication fails at an authentication method, the device stops; it does not
continue and does not attempt to use the next authentication method.
Defining authentication methods for access
1.
Click on the chassis and select the
Security
tab.
2.
Click on the icon next to
Authenticate users
. The
Edit authentication types
dialog displays (see the figure
below).
3.
Drag authentication methods into the desired order. Any authentication methods that are not required should be placed
below
And ignore:
, which can also be dragged into position.
The following authentication methods are available:
•
Local
—Username and password is checked against the data stored on the local device. These username and
password pairs are defined in the
Local Users
dialog.
•
RADIUS
—User is authenticated on a RADIUS server. You must have configured one or more RADIUS servers.
•
—User authenticated on the server. You must have configured one or more
authentication servers.
4.
Click
Review/apply
and review pending changes. To apply these changes to the system, click
Apply changes
or click
'
X
' to cancel.