4-36
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 4 Network Address Translation (NAT
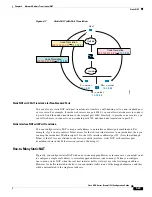
Static NAT
port/mapped destination port; the second service object contains the mapped source port/real
destination port. For identity port translation, simply use the same service object for both the real
and mapped ports (source and/or destination ports, depending on your configuration).
•
Net-to-net—(Optional.) For NAT 46, specify
net-to-net
to translate the first IPv4 address to the first
IPv6 address, the second to the second, and so on. Without this option, the IPv4-embedded method
is used. For a one-to-one translation, you must use this keyword.
•
DNS—(Optional; for a source-only rule.) The
dns
keyword translates DNS replies. Be sure DNS
inspection is enabled (it is enabled by default). You cannot configure the
dns
keyword if you
configure a
destination
address. See
for more information.
•
Unidirectional—(Optional.) Specify
unidirectional
so the destination addresses cannot initiate
traffic to the source addresses.
•
No Proxy ARP—(Optional.) Specify
no-proxy-arp
to disable proxy ARP for incoming packets to
the mapped IP addresses. See
Mapped Addresses and Routing, page 5-12
for more information.
•
Inactive—(Optional.) To make this rule inactive without having to remove the command, use the
inactive
keyword. To reactivate it, reenter the whole command without the
inactive
keyword.
•
Description—Optional.) Provide a description up to 200 characters using the
description
keyword.
Examples
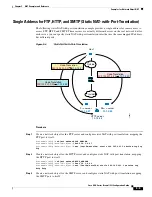
The following example shows the use of static interface NAT with port translation. Hosts on the outside
access an FTP server on the inside by connecting to the outside interface IP address with destination port
65000 through 65004. The traffic is untranslated to the internal FTP server at 192.168.10.100:6500
through 65004. Note that you specify the source port range in the service object (and not the destination
port) because you want to translate the source address and port as identified in the command; the
destination port is “any.” Because static NAT is bidirectional, “source” and “destination” refers primarily
to the command keywords; the actual source and destination address and port in a packet depends on
which host sent the packet. In this example, connections are originated from outside to inside, so the
“source” address and port of the FTP server is actually the destination address and port in the originating
packet.
hostname(config)#
object service FTP_PASV_PORT_RANGE
hostname(config-service-object)#
service tcp source range 65000 65004
hostname(config)#
object network HOST_FTP_SERVER
hostname(config-network-object)#
host 192.168.10.100
hostname(config)#
nat (inside,outside) source static HOST_FTP_SERVER interface
service FTP_PASV_PORT_RANGE FTP_PASV_PORT_RANGE
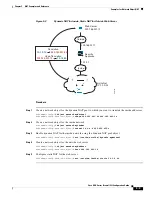
The following example shows a static translation of one IPv6 network to another IPv6 when accessing
an IPv6 network, and the dynamic PAT translation to an IPv4 PAT pool when accessing the IPv4 network:
hostname(config)#
object network INSIDE_NW
hostname(config-network-object)#
subnet 2001:DB8:AAAA::/96
hostname(config)#
object network MAPPED_IPv6_NW
hostname(config-network-object)#
subnet 2001:DB8:BBBB::/96
hostname(config)#
object network OUTSIDE_IPv6_NW
hostname(config-network-object)#
subnet 2001:DB8:CCCC::/96
hostname(config)#
object network OUTSIDE_IPv4_NW
hostname(config-network-object)#
subnet 10.1.1.0 255.255.255.0
Содержание ASA 5512-X
Страница 5: ...P A R T 1 Service Policies and Access Control ...
Страница 6: ......
Страница 50: ...3 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 3 Access Rules History for Access Rules ...
Страница 51: ...P A R T 2 Network Address Translation ...
Страница 52: ......
Страница 126: ...5 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 5 NAT Examples and Reference DNS and NAT ...
Страница 127: ...P A R T 3 Application Inspection ...
Страница 128: ......
Страница 255: ...P A R T 4 Connection Settings and Quality of Service ...
Страница 256: ......
Страница 288: ...12 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 12 Quality of Service History for QoS ...
Страница 303: ...P A R T 5 Advanced Network Protection ...
Страница 304: ......
Страница 339: ...P A R T 6 ASA Modules ...
Страница 340: ......
Страница 398: ...17 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 17 ASA CX Module History for the ASA CX Module ...