5-10
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 5 NAT Examples and Reference
NAT in Routed and Transparent Mode
NAT in Routed Mode
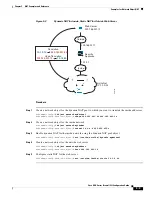
The following figure shows a typical NAT example in routed mode, with a private network on the inside.
Figure 5-8
NAT Example: Routed Mode
1.
When the inside host at 10.1.2.27 sends a packet to a web server, the real source address of the
packet, 10.1.2.27, is changed to a mapped address, 209.165.201.10.
2.
When the server responds, it sends the response to the mapped address, 209.165.201.10, and the
ASA receives the packet because the ASA performs proxy ARP to claim the packet.
3.
The ASA then changes the translation of the mapped address, 209.165.201.10, back to the real
address, 10.1.2.27, before sending it to the host.
NAT in Transparent Mode
Using NAT in transparent mode eliminates the need for the upstream or downstream routers to perform
NAT for their networks.
NAT in transparent mode has the following requirements and limitations:
•
Because the transparent firewall does not have any interface IP addresses, you cannot use interface
PAT.
•
ARP inspection is not supported. Moreover, if for some reason a host on one side of the ASA sends
an ARP request to a host on the other side of the ASA, and the initiating host real address is mapped
to a different address on the same subnet, then the real address remains visible in the ARP request.
•
Translating between IPv4 and IPv6 networks is not supported. Translating between two IPv6
networks, or between two IPv4 networks is supported.
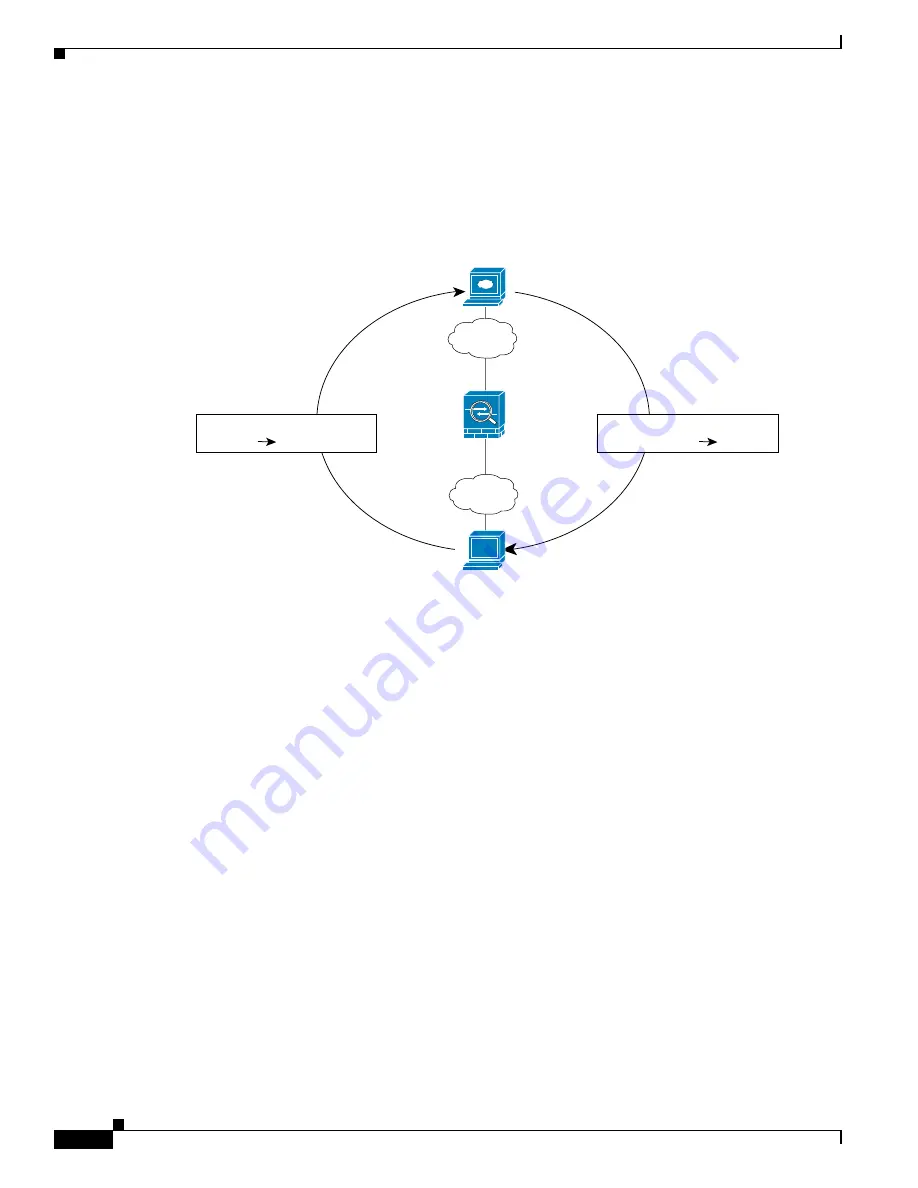
The following figure shows a typical NAT scenario in transparent mode, with the same network on the
inside and outside interfaces. The transparent firewall in this scenario is performing the NAT service so
that the upstream router does not have to perform NAT.
Web
S
erver
www.ci
s
co.com
O
u
t
s
ide
In
s
ide
209.165.201.2
10.1.2.1
10.1.2.27
1
3
002
3
Tr
a
n
s
l
a
tion
209.165.201.10
10.1.2.27
Origin
a
ting
P
a
cket
Undo Tr
a
n
s
l
a
tion
209.165.201.10
10.1.2.27
Re
s
ponding
P
a
cket
S
ec
u
rity
Appli
a
nce
Содержание ASA 5512-X
Страница 5: ...P A R T 1 Service Policies and Access Control ...
Страница 6: ......
Страница 50: ...3 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 3 Access Rules History for Access Rules ...
Страница 51: ...P A R T 2 Network Address Translation ...
Страница 52: ......
Страница 126: ...5 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 5 NAT Examples and Reference DNS and NAT ...
Страница 127: ...P A R T 3 Application Inspection ...
Страница 128: ......
Страница 255: ...P A R T 4 Connection Settings and Quality of Service ...
Страница 256: ......
Страница 288: ...12 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 12 Quality of Service History for QoS ...
Страница 303: ...P A R T 5 Advanced Network Protection ...
Страница 304: ......
Страница 339: ...P A R T 6 ASA Modules ...
Страница 340: ......
Страница 398: ...17 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 17 ASA CX Module History for the ASA CX Module ...