13-2
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 13 Troubleshooting Connections and Resources
Testing Your Configuration
You can using ping to do the following tests:
•
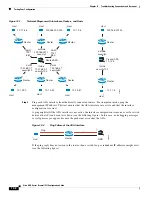
Loopback testing of two interfaces—You can initiate a ping from one interface to another on the
same ASA, as an external loopback test to verify basic “up” status and operation of each interface.
•
Pinging to an ASA—You can ping an interface on another ASA to verify that it is up and responding.
•
Pinging through an ASA—You can ping through an intermediate ASA by pinging a device on the
other side of the ASA. The packets will pass through two of the intermediate ASA’s interfaces as
they go in each direction. This action performs a basic test of the interfaces, operation, and response
time of the intermediate unit.
•
Pinging to test questionable operation of a network device—You can ping from an ASA interface to
a network device that you suspect is functioning incorrectly. If the interface is configured correctly
and an echo is not received, there might be problems with the device.
•
Pinging to test intermediate communications—You can ping from an ASA interface to a network
device that is known to be functioning correctly. If the echo is received, the correct operation of any
intermediate devices and physical connectivity is confirmed.
Choosing Between ICMP and TCP Ping
The ASA includes the traditional ping, which sends ICMP Echo Request packets and gets Echo Reply
packets in return. This is the standard tool and works well if all intervening network devices allow ICMP
traffic. With ICMP ping, you can ping IPv4 or IPv6 addresses, or host names.
However, some networks prohibit ICMP. If this is true of your network, you can instead use TCP ping
to test network connectivity. With TCP ping, the ping sends TCP SYN packets, and considers the ping a
success if it receives a SYN-ACK in response. With TCP ping, you can ping IPv4 addresses or host
names, but you cannot ping IPv6 addresses.
Keep in mind that a successful ICMP or TCP ping simply means that the address you are using is alive
and responding to that specific type of traffic. This means that basic connectivity is working. Other
policies running on a device could prevent specific types of traffic from successfully getting through a
device.
Enable ICMP
By default, you can ping from a high security interface to a low security interface. You just need to
enable ICMP inspection to allow returning traffic through. If you want to ping from low to high, then
you need to apply an ACL to allow traffic.
When pinging an ASA interface, any ICMP rules applied to the interface must allow Echo Request and
Echo Response packets. ICMP rules are optional: if you do not configure them, all ICMP traffic to an
interface is allowed.
This procedure explains all of ICMP configuration you might need to complete to enable ICMP pinging
of ASA interfaces, or for pinging through an ASA.
Procedure
Step 1
Ensure ICMP rules allow Echo Request/Echo Response.
ICMP rules are optional and apply to ICMP packets sent directly to an interface. If you do not apply
ICMP rules, all ICMP access is allowed. In this case, no action is required.
However, if you do implement ICMP rules, ensure that you include at least the following on each
interface, replacing “inside” with the name of an interface on your device.
Содержание ASA 5512-X
Страница 5: ...P A R T 1 Service Policies and Access Control ...
Страница 6: ......
Страница 50: ...3 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 3 Access Rules History for Access Rules ...
Страница 51: ...P A R T 2 Network Address Translation ...
Страница 52: ......
Страница 126: ...5 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 5 NAT Examples and Reference DNS and NAT ...
Страница 127: ...P A R T 3 Application Inspection ...
Страница 128: ......
Страница 255: ...P A R T 4 Connection Settings and Quality of Service ...
Страница 256: ......
Страница 288: ...12 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 12 Quality of Service History for QoS ...
Страница 303: ...P A R T 5 Advanced Network Protection ...
Страница 304: ......
Страница 339: ...P A R T 6 ASA Modules ...
Страница 340: ......
Страница 398: ...17 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 17 ASA CX Module History for the ASA CX Module ...