6-2
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 6 Getting Started with Application Layer Protocol Inspection
Application Layer Protocol Inspection
•
Connections (XLATE and CONN tables)—Maintains state and other information about each
established connection. This information is used by the Adaptive Security Algorithm and
cut-through proxy to efficiently forward traffic within established sessions.
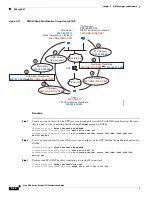
Figure 6-1
How Inspection Engines Work
In this figure, operations are numbered in the order they occur:
1.
A TCP SYN packet arrives at the ASA to establish a new connection.
2.
The ASA checks the ACL database to determine if the connection is permitted.
3.
The ASA creates a new entry in the connection database (XLATE and CONN tables).
4.
The ASA checks the Inspections database to determine if the connection requires application-level
inspection.
5.
After the application inspection engine completes any required operations for the packet, the ASA
forwards the packet to the destination system.
6.
The destination system responds to the initial request.
7.
The ASA receives the reply packet, looks up the connection in the connection database, and
forwards the packet because it belongs to an established session.
The default configuration of the ASA includes a set of application inspection entries that associate
supported protocols with specific TCP or UDP port numbers and that identify any special handling
required.
When to Use Application Protocol Inspection
When a user establishes a connection, the ASA checks the packet against ACLs, creates an address
translation, and creates an entry for the session in the fast path, so that further packets can bypass
time-consuming checks. However, the fast path relies on predictable port numbers and does not perform
address translations inside a packet.
Many protocols open secondary TCP or UDP ports. The initial session on a well-known port is used to
negotiate dynamically assigned port numbers.
1
3
2
8
75
1
7
6
5
2
3
4
Client
ACL
XLATE
CONN
In
s
pection
S
erver
A
S
A
Содержание ASA 5512-X
Страница 5: ...P A R T 1 Service Policies and Access Control ...
Страница 6: ......
Страница 50: ...3 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 3 Access Rules History for Access Rules ...
Страница 51: ...P A R T 2 Network Address Translation ...
Страница 52: ......
Страница 126: ...5 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 5 NAT Examples and Reference DNS and NAT ...
Страница 127: ...P A R T 3 Application Inspection ...
Страница 128: ......
Страница 255: ...P A R T 4 Connection Settings and Quality of Service ...
Страница 256: ......
Страница 288: ...12 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 12 Quality of Service History for QoS ...
Страница 303: ...P A R T 5 Advanced Network Protection ...
Страница 304: ......
Страница 339: ...P A R T 6 ASA Modules ...
Страница 340: ......
Страница 398: ...17 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 17 ASA CX Module History for the ASA CX Module ...