14-2
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 14 ASA and Cisco Cloud Web Security
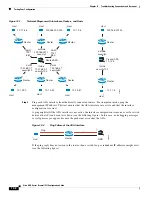
Information About Cisco Cloud Web Security
•
•
Failover from Primary to Backup Proxy Server, page 14-4
User Identity and Cloud Web Security
You can use user identity to apply policy in Cloud Web Security. User identity is also useful for Cloud
Web Security reporting. User identity is not required to use Cloud Web Security. There are other methods
to identify traffic for Cloud Web Security policy.
You can use the following methods of determining the identity of a user or of providing a default identity:
•
Identity firewall—When the ASA uses identity firewall with Active Directory (AD), the username
and group is retrieved from the AD agent. Users and groups are retrieved when you use them in an
ACL in a feature such as an access rule or in your service policy, or by configuring the user identity
monitor to download user identity information directly.
For information about configuring IDFW, see the general operations configuration guide.
•
AAA rules—When the ASA performs user authentication using a AAA rule, the username is
retrieved from the AAA server or local database. Identity from AAA rules does not include group
information. If you configure a default group, these users are associated with that default group. For
information about configuring AAA rules, see the legacy feature guide.
•
Default username and group—For traffic that does not have an associated user name or group, you
can configure an optional default username and group name. These defaults are applied to all users
that match a service policy rule for Cloud Web Security.
Authentication Keys
Each ASA must use an authentication key that you obtain from Cloud Web Security. The authentication
key lets Cloud Web Security identify the company associated with web requests and ensures that the
ASA is associated with a valid customer.
You can use one of two types of authentication keys for your ASA: the company key or the group key.
•
Company authentication key
—You can use a company authentication key on multiple ASAs
within the same company. This key simply enables the Cloud Web Security service for your ASAs.
•
Group authentication key
—A Group authentication key is a special key unique to each ASA that
performs two functions:
–
Enables the Cloud Web Security service for one ASA.
–
Identifies all traffic from the ASA so you can create ScanCenter policy per ASA.
You generate these keys in ScanCenter (
https://scancenter.scansafe.com/portal/admin/login.jsp
). For
more information, see the Cloud Web Security documentation:
ScanCenter Policy
In ScanCenter, traffic is matched against policy rules in order until a rule is matched. Cloud Web Security
then applies the configured action for the rule, allowing or blocking the traffic, or warning the user. With
warnings, the user has the option to continue on to the web site.
Содержание ASA 5512-X
Страница 5: ...P A R T 1 Service Policies and Access Control ...
Страница 6: ......
Страница 50: ...3 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 3 Access Rules History for Access Rules ...
Страница 51: ...P A R T 2 Network Address Translation ...
Страница 52: ......
Страница 126: ...5 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 5 NAT Examples and Reference DNS and NAT ...
Страница 127: ...P A R T 3 Application Inspection ...
Страница 128: ......
Страница 255: ...P A R T 4 Connection Settings and Quality of Service ...
Страница 256: ......
Страница 288: ...12 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 12 Quality of Service History for QoS ...
Страница 303: ...P A R T 5 Advanced Network Protection ...
Страница 304: ......
Страница 339: ...P A R T 6 ASA Modules ...
Страница 340: ......
Страница 398: ...17 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 17 ASA CX Module History for the ASA CX Module ...