1-17
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 1 Service Policy Using the Modular Policy Framework
Configure Service Policies
Step 2
Specify a previously configured Layer 3/4 class map, where the
class_map_name
is the name of the class
map.
class
class_map_name
See
Identify Traffic (Layer 3/4 Class Maps), page 1-13
to add a class map.
Note
If there is no
match default-inspection-traffic
command in a class map, then at most one
inspect
command is allowed to be configured under the class.
class
class_map_name
Example:
hostname(config-pmap)# description global policy map
Step 3
Specify one or more actions for this class map.
See
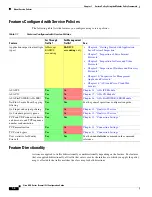
Features Configured with Service Policies, page 1-4
.
Step 4
Repeat the process for each class map you want to include in this policy map.
Examples
The following is an example of a
policy-map
command for a connection policy. It limits the number of
connections allowed to the web server 10.1.1.1:
hostname(config)#
access-list http-server permit tcp any host 10.1.1.1
hostname(config)#
class-map http-server
hostname(config-cmap)#
match access-list http-server
hostname(config)#
policy-map global-policy
hostname(config-pmap)#
description This policy map defines a policy concerning connection
to http server.
hostname(config-pmap)#
class http-server
hostname(config-pmap-c)#
set connection conn-max 256
The following example shows how multi-match works in a policy map:
hostname(config)#
class-map inspection_default
hostname(config-cmap)#
match default-inspection-traffic
hostname(config)#
class-map http_traffic
hostname(config-cmap)#
match port tcp eq 80
hostname(config)#
policy-map outside_policy
hostname(config-pmap)#
class inspection_default
hostname(config-pmap-c)#
inspect http http_map
hostname(config-pmap-c)#
inspect sip
hostname(config-pmap)#
class http_traffic
hostname(config-pmap-c)#
set connection timeout idle 0:10:0
The following example shows how traffic matches the first available class map, and will not match any
subsequent class maps that specify actions in the same feature domain:
hostname(config)#
class-map telnet_traffic
hostname(config-cmap)#
match port tcp eq 23
hostname(config)#
class-map ftp_traffic
hostname(config-cmap)#
match port tcp eq 21
hostname(config)#
class-map tcp_traffic
hostname(config-cmap)#
match port tcp range 1 65535
hostname(config)#
class-map udp_traffic
hostname(config-cmap)#
match port udp range 0 65535
hostname(config)#
policy-map global_policy
Содержание ASA 5512-X
Страница 5: ...P A R T 1 Service Policies and Access Control ...
Страница 6: ......
Страница 50: ...3 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 3 Access Rules History for Access Rules ...
Страница 51: ...P A R T 2 Network Address Translation ...
Страница 52: ......
Страница 126: ...5 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 5 NAT Examples and Reference DNS and NAT ...
Страница 127: ...P A R T 3 Application Inspection ...
Страница 128: ......
Страница 255: ...P A R T 4 Connection Settings and Quality of Service ...
Страница 256: ......
Страница 288: ...12 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 12 Quality of Service History for QoS ...
Страница 303: ...P A R T 5 Advanced Network Protection ...
Страница 304: ......
Страница 339: ...P A R T 6 ASA Modules ...
Страница 340: ......
Страница 398: ...17 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 17 ASA CX Module History for the ASA CX Module ...