4-26
Cisco ASA Series Firewall CLI Configuration Guide
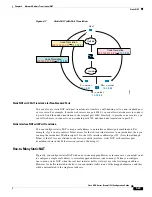
Chapter 4 Network Address Translation (NAT
Dynamic PAT
xlate per-session permit udp any4 any6 eq domain
xlate per-session permit udp any6 any4 eq domain
xlate per-session permit udp any6 any6 eq domain
You cannot remove these rules, and they always exist after any manually-created rules. Because rules
are evaluated in order, you can override the default rules. For example, to completely negate these rules,
you could add the following:
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
Procedure
Step 1
Create a permit or deny per-session PAT rule. This rule is placed above the default rules, but below any
other manually-created rules. Be sure to create your rules in the order you want them applied.
xlate per-session
{
permit
|
deny
} {
tcp
|
udp
}
source_ip
[
operator src_port
]
destination_ip
[
operator dest_port
]
Example
hostname(config)# xlate per-session deny tcp any4 209.165.201.3 eq 1720
For the source and destination IP addresses, you can configure the following:
•
host
ip_address
—Specifies an IPv4 or IPv6 host address.
•
ip_address mask
—Specifies an IPv4 network address and subnet mask.
•
ipv6-address
/
prefix-length
—Specifies an IPv6 network address and prefix.
•
any4
and
any6
—
any4
specifies only IPv4 traffic; and
any6
specifies any6 traffic.
The
operator
matches the port numbers used by the source or destination. The default is all ports. The
permitted operators are:
•
lt
—less than
•
gt
—greater than
•
eq
—equal to
•
neq
—not equal to
•
range
—an inclusive range of values. When you use this operator, specify two port numbers, for
example,
range 100 200
.
Examples
The following example creates a deny rule for H.323 traffic, so that it uses multi-session PAT:
hostname(config)# xlate per-session deny tcp any4 209.165.201.7 eq 1720
hostname(config)# xlate per-session deny udp any4 209.165.201.7 range 1718 1719
Содержание ASA 5512-X
Страница 5: ...P A R T 1 Service Policies and Access Control ...
Страница 6: ......
Страница 50: ...3 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 3 Access Rules History for Access Rules ...
Страница 51: ...P A R T 2 Network Address Translation ...
Страница 52: ......
Страница 126: ...5 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 5 NAT Examples and Reference DNS and NAT ...
Страница 127: ...P A R T 3 Application Inspection ...
Страница 128: ......
Страница 255: ...P A R T 4 Connection Settings and Quality of Service ...
Страница 256: ......
Страница 288: ...12 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 12 Quality of Service History for QoS ...
Страница 303: ...P A R T 5 Advanced Network Protection ...
Страница 304: ......
Страница 339: ...P A R T 6 ASA Modules ...
Страница 340: ......
Страница 398: ...17 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 17 ASA CX Module History for the ASA CX Module ...